DMA stands for Direct Memory Access, a capability in modern computers that allows peripheral devices to send data to the motherboard’s memory without intervention from the CPU. The DMA controllers are special hardware – now embedded into the chip in modern integrated processors – that manage the data transfers and arbitrate access to the system bus. The controllers are programmed with source and destination pointers (where to read/write the data), counters to track the number of transferred bytes, and settings, which includes I/O and memory types, interrupts and states for Read More
Error 88780078
Error 88780078 may occur on Windows computers when attempting to play audio files. This indicates that there is a bad DirectSound driver on the computer. This error is most commonly associated with using WinAmp to play audio files on Windows XP, Vista, or Windows 7. Though this is the case, other audio players can also trigger this error. How to Fix Error 88780078 Step 1 – Select “Start,” “Settings,” and “Control Panel” to open the “Control Panel.” Step 2 – Select the “Audio” menu tab and verify the information listed Read More
How MS Access Encryption Works

Microsoft Access had no encryption capability until the release of Microsoft Access 2007. With the MS Access 2007 release, encryption is now available. Encryption Requirements To encrypt your access database you must use a new database format released with MS Access 2007, the ACCDB format. Differences between the original MDB format and the new ACCDB format can be found here. If you need to convert your older database to the ACCDB format perform these operations: Open Microsoft Access 2007. Click the “Microsoft Office Button”. It should be in the left Read More
Java Operators

Java Operator Operator Description [ ] Array index () Method call . Member access ++ Prefix or postfix increment — Prefix or postfix decrement + – Unary plus, minus ~ Bitwise NOT ! Boolean (logical) NOT (type) Type cast new Object creation * / % Multiplication, division, remainder + – Addition, subtraction + String concatenation << Signed bit shift left to right >> Signed bit shift right to left >>> Unsigned bit shift right to left < <= Less than, less than or equal to > >= Greater than, greater Read More
Free FTP Software
FTP software is divided into two categories: FTP server and FTP clients. Server software is necessary to run an FTP server; Client software is necessary to transfer files to and from an FTP server. Almost all versions of Unix ship with a free FTP server and a free FTP client. Microsoft Windows ships with a free FTP client, but without an FTP server. The basic FTP clients tend to provide only a Command Line Interface (CLI), which is not terribly user friendly. Luckily, both free and commercial FTP clients are Read More
How Does a Segway Work?

A Segway is a vertical, mobile vehicle that is able to carry a single person between distances. While a bicycle consists of two wheels and a horizontal frame, a Segway consists of two or four wheels and a vertical frame that balances atop these wheels to steady the rider. Segways run on purely electrical energy and can be taken anywhere pedestrians can go. Segways are large enough to transport a person and yet light enough to carry in one arm. Dynamic Stabilization Dynamic stabilization involves the use of sensors that Read More
MySpace Proxy

Almost every anonymous proxy on the Internet runs either PHProxy or CGIProxy. You cannot access MySpace anonymously using a PHProxy. PHProxy removes all traces of anonymity whilst having Client-Side Scripting enabled. CGIProxy has Client-Side Scripting Enabled and still offers full anonymity. You can still use PHProxy to access MySpace, but you will not be anonymous. Why CGIProxy? CGIProxy offers full anonymity, no matter what it is that you do with it (unless the code has been edited to use PHP/MySQL queries); a PHProxy only offers full anonymity when the default Read More
VPN Servers
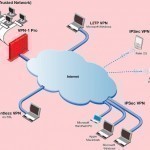
A VPN (Virtual Private Network) server is one that is connected to a Virtual Private Network in order to allow remote users to access files on the server. Companies, government agencies, and various institutions use VPN servers in order to provide users who are away from the server with consistent access to important files and software. Likewise, VPN servers are used domestically to ensure that users have access to computer files while they are away from their home or office. How VPN Servers Work A VPN server is simply one Read More
Document Management System

In the information age, the process of input, delivery, storage, receipt, and categorization of data is critical. Companies, government entities, and individuals have to rely more and more on automated, reliable solutions in order to keep their information safe and readily accessible. A document management system (DMS) is an integrated network of compatible programs or computer systems that reliably handle information for accurate records and usability. As more data is created and shared on a daily basis there is a great demand on keeping it secure and available. Document management Read More
Packet Sniffing
Packet sniffing is the act of intercepting and recording traffic that passes over a specific section or location on a network. As the data passes across the network, a packet sniffer application saves each packet for later use. Network administrators and law enforcement packet sniff for legitimate reasons, but rogue actors who use the captured traffic to steal private and corporate information also use it. How does Packet Sniffing Work? In normal network operations, a computer or networked device only looks at network packets that are addressed to the respective Read More


Share on: