A microchip, commonly called the integrated circuit, is a tiny electronic circuit. It is made up primarily of semiconductor devices. For the most part, these small microchips are used in nearly every type of electronic device known to man. As the years have gone on from their creation in the late 50s and early 60s, the microchip has become much smaller and more inexpensive to make. Because of this, it has allowed more users to gain access to greater types of electronics. The History of the Microchip In 1968, Jack Read More
Bokode
A bokode is a new type of technology that was developed by a team at the MIT media lab. A bokode is a digital tag that, like a barcode, can be used to hold information. However, unlike a barcode, a bokode can hold thousands of times of more information than a barcode and can be much smaller than a barcode. A bokode is circular in shape with a diameter of about 3mm. In other words, it is an incredibly small blip that holds considerable amounts of information that the team Read More
PC Based Machine Controls

PC Based Machine controls are fairly new to industrial environments, however, within the last two decades, PC based machine controls have overtaken the once standard PLC (programmable logic controllers) to run many industrial processes. A machine control is an essential part of modern industrial processes and automation. If you have never visited a factory or assembly line, many of today’s vital components of manufacturing no longer require a human, they are instead computer controlled. While each manufacturer and sometimes each industrial process once required a special PLC with specific hardware Read More
VoIP QoS

VoIP QoS (Voice over Internet Protocol Quality of Service) is used in VoIP services to determine a VoIP network’s overall performance and make changes to increase the customer satisfaction rate. QoS is used in other systems (like computer networks) as well, but is especially important in VoIP services because of the high demand for prompt, real-time voice packet delivery and call handling. VoIP QoS generally refers to the VoIP system’s bit rate, delay, and bit error rate and provides customers with a realistic idea of the VoIP network’s capabilities. How Read More
What Causes Volcanoes?
Volcanoes are caused by plate tectonics. The entire world is covered in plates that move around due to high pressures underneath them. Depending on the plates, they may rub together resulting in friction or they spread apart resulting in a gap between the two plates. This results in two different types of volcanoes. There are cone-shaped volcanoes, the ones that are similar to mountains, and then there are crack volcanoes, typically only seen under water. Cone Shaped Volcanoes A cone shaped volcanoes is formed when two plates start to rub Read More
WMV Files

WMV (Windows Media Video) is a generic name for video encoding solutions that Microsoft developed. The format is a part of the Windows Media framework that also includes formats like Windows Media Audio (WMA), Advanced Systems Format (ASF), and High Definition Photo (HDP). WMV files use the Microsoft container format and represent Microsoft’s own version of MPEG-4 (Part 2) video encoding technology. First introduced in 1999, the WMV format now competes with other codecs such as DivX and RealVideo as a means of distributing video content on the World Wide Read More
How to Change an AOL Password

There are two circumstances that can cause someone to want to change his/her AOL password: 1) forgetting the AOL password and needing to recover it and 2) to change the AOL password. The latter can be because the AOL password has leaked to someone or the user wants to adhere to the good practice of changing his/her password periodically. It is a good practice to change one’s AOL password at least once in a month. Changing an AOL Password The following steps show in detail how to change an AOL Read More
Inter-Process Communication
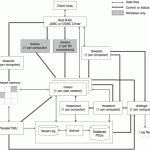
The term Inter-Process Communication (IPC) refers to a predefined library or set of interfaces that allow processes to communicate with each other. IPC gives the appearance of programs that run concurrently in an operating system’s background and allows computer users to conduct multiple tasks at once on a computer. IPCs can share memory, run in synchrony with other processes, pass messages, and conduct remote procedure calls. The specific IPC method varies based on the Operating System (OS), latency of communication between program threads, and the type of information being exchanged Read More
How to Unlock an iPod Touch
Have you locked your iPod Touch with a passcode and forgotten what that passcode is? Are you considering throwing it away due to the fact that it is no longer operational? Well, you’re in luck. Throw away that idea because you can actually restore your iPod Touch back to factory settings, in turn removing the passcode that was previously there. The downside to this is that you will need to retrieve your files before doing so, unless the files that are on your iPod have already been backed up. How Read More
Auditing Security Events
An Overview of Auditing Auditing enables you to determine which activities are occurring on your system. Through auditing, you can track access to objects, files and folders; as well as any modifications made to the objects, files and folders. Auditing therefore enables you to collect information associated with resource access and usage on your system by allowing you to audit system logon, file access, object access, as well as any configuration changes. An audit trail can be defined as a list of audit entries which portray the life span of Read More


Share on: