Packet Sniffing
Packet sniffing is the act of intercepting and recording traffic that passes over a specific section or location on a network. As the data passes across the network, a packet sniffer application saves each packet for later use. Network administrators and law enforcement packet sniff for legitimate reasons, but rogue actors who use the captured traffic to steal private and corporate information also use it.
How does Packet Sniffing Work?
In normal network operations, a computer or networked device only looks at network packets that are addressed to the respective device. The remaining network traffic is ignored. A packet sniffer is setup in promiscuous mode on a network in order to record all network traffic that it sees. Depending on the packet sniffer’s location on the local network, the amount of traffic that it sniffs or sees varies significantly. Packet sniffing applications can be setup to record all traffic in an “unfiltered” mode or a subset of network traffic in “filtered” mode that meets specific data thresholds for being recorded. The data can then be stored in memory, on a hard drive, or even transmitted to a remote receiver depending on the specific packet sniffing program being used.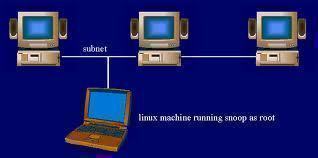
What are the uses for Packet Sniffing?
There are several uses for packet sniffing. Many ISPs use packet sniffers as network diagnostic tools. They maintain copies of data, email, and websites that users visit on their respective networks. Packet sniffing is also used to troubleshoot network issues and to conduct traffic analysis to help ensure that the quality of service metrics on a network are met. Packet sniffing can also be used to capture personal information such as account passwords, banking information, and email content that can then be used for identity theft, privacy invasion, and other malicious purposes.
How can One Defend Against Packet Sniffing?
The best way to defend against packet sniffing is to encrypt email. When strong enough encryption is used, packet sniffers can only determine an email’s destination address. The data can still be “Sniffed” or captured, but the encryption would have to be broken for the email to be read. Similarly, when passing sensitive information over the Internet, it is required that a website that supports a secure connection through the “HTTPS” protocol is used in order to prevent a packet sniffer from capturing information. A popular email encryption program that consumers use to defend against packet sniffing is the PGP (Pretty Good Privacy) standard. It has an email plug-in that is compatible with many of the major email clients.


Comments - No Responses to “Packet Sniffing”
Sorry but comments are closed at this time.