Tree and Forest in Active Directory
The Domain is the core unit of logical structure in Active Directory. All objects that share a common directory database and trust relationship with other domain and security policies are known as Domains. Each domain stores information only about the objects that belong to that domain.
All security polices and settings, such as administrative rights, security policies, and Access Control Lists (ACLs), do not cross from one domain to another. Thus, a domain administrator has full rights to set policies only within domain they belong to.
Domains provide administrative boundaries for objects and manage security for shared resources and a replication unit for objects.
A Tree
Trees are collections of one or more domains that allow global resource sharing. A tree may consist of a single domain or multiple domains in a contiguous namespace. A domain added to a tree becomes a child of the tree root domain. The domain to which a child domain is attached is called a parent domain. A child domain can also have its multiple child domains. Child domain uses the name then its parent domain name and gets a unique Domain Name System (DNS).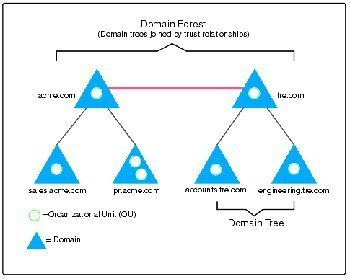
For example, if tech.com is the root domain, users can create one or more Child domains to tech.com such as north.tech.com and or south.tech.com. These “children” may also have child domains created under them, such as sales.north.tech.com.
The domains in a tree have two way, Kerberos transitive trust relationships. A Kerberos transitive trust simply means that if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A trusts Domain C. Therefore, a domain joining a tree immediately has trust relationships established with every domain in the tree.
A Forest
A forest is a collection of multiple trees that share a common global catalog, directory schema, logical structure, and directory configuration. Forest has automatic two way transitive trust relationships. The very first domain created in the forest is called the forest root domain.
Forests allow organizations to group their divisions that use different naming schemes and may need to operate independently. But as an organization, they want to communicate with the entire organization via transitive trusts and share the same schema and configuration container.


Comments - 17 Responses to “Tree and Forest in Active Directory”
Sorry but comments are closed at this time.