PKI Certificate
A PKI certificate, which stands for Public Key Infrastructure certificate, allows someone to combine their digital signature with a public key and something that identifies them, an example being their real life name. This certificate is used to allow computer users to show that they do own the public keys they claim to. In other words, it is a security mechanism for public keys.
As mentioned before, a digital signature is required for the PKI certificate. This signature can either be made by an authority figure who assigns the certificates, the person whose identity is being confirmed, or even endorsers of the public key. As with credit cards, a digital signature is a way for other parties and people to verify that a person is in fact the owner of the public key they claim is their own.
Applications of PKI Certificates
PKI certificates are most commonly used to authenticate cryptographic public keys. In small networks, giving public keys to others may be safe. This is often untrue for larger networks, however, and a solution must be found. This solution is public-key cryptography.
To give an example of why having an unsecured public key may become troublesome, let us take the example that a person needs to communicate with another person in order to establish a business relationship. By publishing his public key, the first person is able to receive and send messages to his companion through a secure and safe method. A problem arises, however, in the fact that someone else can pose as the first person and send messages that person did not want to send. I am sure it becomes obvious why a person pretending to be another can be a huge problem during any sort of communication effort.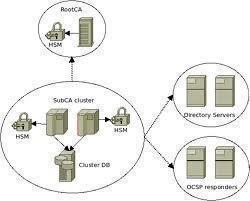
The PKI certificate is a way to stop this problem. This certificate allows other people to verify that they are indeed communicating with the right person and using the right public key. It is a clear answer to the problem of the third party problems that may arise without it.
Multiple Certificate Authorities
A problem can occur when two different people or parties meet each other and both are using certification authorities the other does not recognize. Because they do not recognize the respective authorities, the certificates may not seem real. To help combat this, many certificate authorities now keep their own personal public keys in the certificates to help guide new finders of their services to them. This public key is signed by yet another certification authority, allowing a complicated hierarchy of trust to be created. To keep this simple, it basically means that all certificates are linked together by one source in an ideal situation and this source is a trustworthy one.
It is important for users who are given PKI certificates to ensure that his or her certification authority is indeed a legitimate provider of that service. It can obviously lead to problems if someone is using a certificate that really has no use as it was given out by someone lacking the authority to. Use the Certificate Revocation List or the Online Certificate Status Protocol to check this information.
PKI Certificate Revokation
There are times when a certificate must be revoked by an authority. A common example of this occurring is if a person’s identity information changes, for instance if they decide to change their name for some reason or another.
PKI Certificate Standards
The PKI certificate usually includes personal information such as name, employment status and company’s name, and how long the certificate is valid. The most popular standard for PKI certificates is ITU-T X.509.


Comments - One Response to “PKI Certificate”
Sorry but comments are closed at this time.