Access control is the execution of limitations and restrictions on whoever tries to occupy a certain protected property, thereby keeping people as safe as possible. As modern society moves further into the cyber age, these access control systems become almost completely computer controlled. This article will further explain what access control is, how it works, and will list the different types. What is Access Control? Access control is the term used to describe how a person, mechanical device, or computer system uses both physical barriers and alarms to keep an Read More
How to Clear the ARP Cache
ARP (Address Resolution Protocol) Cache is a technique used to store “mappings” of OSI Model Network Layer addresses (IP addresses) to corresponding OSI Model Data Link addresses (MAC addresses). Due to a variety of possible circumstances, ARP cache can become damaged requiring the end user or administrator to determine how to clear the ARP cache for the respective computer system or device. Symptoms that the ARP cache requires clearing include the computer’s operating system failing to function properly, numerous websites failing to load, and interruptions in network or Internet connectivity. Read More
Spanning Tree Protocol
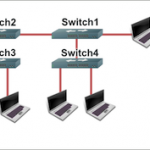
Redundant Topology A Local Area Network may consist of more than one segment. Each segment of the LAN connected through a separate physical device mostly switch. Switches use their uplink ports to connect different segments. The LAN administrator can connect the switches with each other through more than one uplink port using redundant topology. Redundant topology eliminates the single point of failure and that will improve the performance of network. Overall redundant topology is a good solution for making a LAN efficient but there are some drawbacks of redundant topology. Read More
W-CDMA (Wideband Code Division Multiple Access)
WCDMA (Wideband Code Division Multiple Access) is the radio access scheme used for third generation cellular systems that are being rolled out in various parts of the globe. The 3G systems support wide band services like high speed Internet access and video and high quality image transmission with the same quality as the fixed networks. In WCDMA systems, the CDMA air interface is combined with GSM based networks. The WCDMA standard evolved through the Third Generation Partnership Project (3GPP), which aims to ensure interoperability between different 3G networks. The standard Read More
Physical Layer
The Physical Layer is the lowest layer in the OSI (Open Systems Interconnection) Model of computer networking and is used to transfer electrical signals that represent data from one place to another. While the Physical Layer does not represent data itself, it does provide a means for that data to move. Essentially, the Physical Layer represents the hardware of a computer network and consists of everything from the circuit boards and wires to the storage devices and media readers. How The Physical Layer Works The Physical Layer consists of Read More
How to Find an SSID Number

Over the past decade, wireless network use has grown from just something done in computer science departments at universities to something done in the home, restaurants, and just about anywhere. SSID (Service Set Identifier) is the term that describes the wireless network name. It distinguishes between networks that may be in range of a device being used to connect to the Internet via wireless connection. The SSID is commonly confused with the network security password. However, it is not used for that purpose. How to Find an SSID Number Windows Read More
VoIP Phones
VoIP phones are telephones which connect to VoIP networks instead of to the PSTN. VoIP phones with Ethernet connections VoIP phones with Wi-Fi / 802.11 connections VoIP phones with dialup modem connections Software VoIP phones VoIP Phones with Ethernet connections A VoIP phone with an Ethernet connection is the easiest type of VoIP telephone to use. Instead of a standard telephone RJ-11 connector to plug into the PSTN, these phones have RJ-45 connectors to plug into Ethernet networks. The Ethernet connection is used to connect these VoIP phones to the Read More
RG-59
The RG-59 cable is a type of coaxial cable that is used to generate low-power video connections. The cable works on two conductors that are based on a single common axis. It is also used for RF signal connections. The RG-59 cable conducts video and radio frequencies at an impedance of around 75 ohms. The RG-59 cable is used for generating short-distance communication. The cable can be used at baseband video frequencies, which is measured from the lowest count of zero and continues to the highest signal frequency. Baseband refers Read More
What is a VPLS?
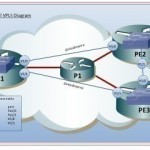
A VPLS (Virtual Private LAN Service) is a network protocol that allows users to connect many different ethernet-based local area networks together over long distances. VPLS uses MPLS data packets and the Internet in order to forward information from one or more computers in one network to one or more computers in another network and then expand that to include even further networks that are all connected via the VPLS. Businesses and government agencies that have branches in many different locations generally use VPLS systems. However VPLS systems can also Read More
2wire Default Password
The 2wire Ethernet client wirelessly connects electronic devices that are not equipped with wireless cards or adapters to a home network. Once configured on a Windows computer, a 2wire card can be used on any device that has an Ethernet connection (e.g. an Xbox 360). A common problem is determining what the 2wire default password is in order to reconfigure or reset the device. What is the 2wire Default Password? For a reconfigured or new 2wire device, the default password is “wireless.” How to Install and Configure 2Wire Step 1 Read More


Share on: