How to Uninstall CyberDefender
CyberDefender is an example of malicious software that poses as an anti-virus software. CyberDefender runs a fake computer scan, then lists a number of “threats” that are really non-existent files, random files, or files that are essential to the computer’s performance. When the user attempts to remove these threats, CyberDefender asks the user to purchase the software. If the user declines, CyberDefender displays a reminder to purchase the software every 30 seconds. CyberDefender also prevents the user from uninstalling the software through conventional means.
Where CyberDefender Comes from
CyberDefender is most often introduced to a computer when someone downloads and installs the program under the assumption that it is a real anti-virus software. This is because CyberDefender is specifically marketed as an anti-virus software and can be found on many websites that allow people to download free software. However, CyberDefender may also be installed on a computer if it is hiding in an unrelated folder or executable file.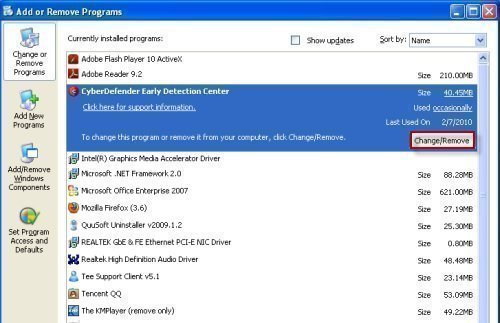
How to Remove CyberDefender
Regardless of how CyberDefender was installed on a computer, there are several methods of removing it, despite the software’s attempts to prevent this. One method of removing CyberDefender is by manually searching for related files and deleting them. However, this can be very time consuming and may be futile if CyberDefender has several copies of itself on the computer or is hiding in a file that does not contain its name. Another method of removing CyberDefender is by running real anti-virus software, such as Spyware Terminator, Malwarebytes’ Antimalware, or Advanced SystemCare. Real anti-virus software may require the user to disable CyberDefender from the computer’s Startup files before it can be completely removed.
How to Prevent Programs from Being Installed
Once CyberDefender is removed, the user should consider implementing a method of preventing similar programs from being installed. In the case of CyberDefender, the software heavily depends on ignorance in order for the user to download and install the program himself/herself. This means that users should always research programs before they download them in order to ensure no malicious programs are ever installed. However, some malicious programs find other ways to enter a computer. Some enter computers through cookies, innocent files, or direct attacks on the user’s firewall. In these cases, regular anti-virus software and/or a real-time shield use should prevent malicious software from being installed.


Comments - 2 Responses to “How to Uninstall CyberDefender”
Sorry but comments are closed at this time.