File Includes in PHP Tutorial This tutorial shows you how to include files in PHP in just a few easy steps. There are four core constructs for including files into your PHP scripts. The main objective is for you to create code in separate files and then be able to use that code to include functions, variables etc., in other PHP scripts. You have two main options. To include() a file or to require() a file. We'll get into the specifics in a moment and you'll quickly understand what the Read More
ITIL Incident Management
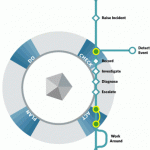
Incident management is a process area found within the ITIL check lists. The goal of any incident management process is to effectively and quickly get a business back to normal service operation. This way, a business’ operations are not impacted as severely. This results in a higher level of service quality. According to ISO 20000, the most important objective of an Incident management team is to “restore agreed service to the business as soon as possible or to respond to service requests.” What is an Incident? An incident is the Read More
Airborne Internet
Airborne Internet refers to installing a broadband network hub in an aircraft flying at 52,000 to 69,000 feet above sea level – high enough to be out of weather disturbances and way outside the flight envelope of commercial aircraft. The aircraft will provide Internet connection to places and establishments within its range. The Need for Airborne Internet Airborne Internet is seen as the perfect answer to the demand for fast, reliable access to the Internet as well as quick and easy file 'sharing.' Currently, the problem lies in the physical Read More
How Thunderstorms Form
There are three stages to a thunderstorm’s life cycle: the cumulus stage, the mature stage, and the dissipation stage. When a thunderstorm begins to form, it does so at the cumulus stage. From there, the storm advances in severity until it reaches its peak at the mature stage and then begins to gradually die out as it enters the dissipation stage. The Cumulus Stage The cumulus stage is the first stage of formation for any thunderstorm and is characterized by a few noticeable factors. First off, a thunderstorm starts by Read More
How Can I Find Someone’s Cell Phone Number?
In this society, almost everyone has a cell phone. To call someone on their cell phone, however, a cell phone number is required. Unless the caller knows the recipient personally, finding his/her cell phone number can be quite frustrating. This article will list a number of ways that the reader can find someone's cell phone number. Local Phonebook If the recipient lives nearby, one source to check for a cell phone number would be the local phonebook. Phonebooks do not always have cell phone numbers listed but it is certainly Read More
How to Add Fractions

The ability to add fractions is a skill that many learn in elementary school and by the time they graduate from high school, seem to have forgotten because it is a skill used so sparsely. However, a quick mind refresh of the steps reveals that adding fractions is a straight forward process that requires three very basic steps. These steps, when combined with an understanding of what a fraction is makes solving addition of fractions very simple. To begin with, a fraction is a part of a whole. For example, Read More
How to Set a Static IP
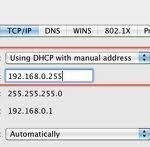
An IP (Internet Protocol) address is a unique identifier for any device that connects to the Internet. All computers, modems, routers, mobile devices, and even accessory items such as printers, scanners, and fax machines have an IP address. IP addresses are extremely common in the web design industry because every website must be associated with a specific server that is identified by its IP address. IP addresses are very important in the information technology era because without them, computers and other devices would not be able to find or access Read More
How to Set Google as the Default Search Engine in Firefox
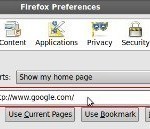
Mozilla Firefox, which the Mozilla Foundation runs and Netscape owns, is a web browser that allows users to take advantage of thousands of add-ons and plug-ins while browsing the web. Since Mozilla Firefox was specifically designed to be both user friendly and functional, Mozilla Firefox users can easily access administrative options from either the Tools menu or the Firefox button. Additionally, users can find step-by-step instructions for most actions in Firefox by visiting Firefox Support. How to Set Google as the Homepage One way to set Google as Firefox’s Read More
Mirroring
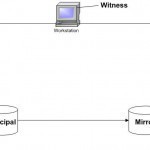
Mirroring is the automated process of writing data to two drives simultaneously. Mirroring is used to provide redundancy, backup, multiple concurrent accesses and uninterrupted accessibility. If one drive fails, the redundant drive will continue to store the data and provide access to it. The failed drive can then be replaced and the drive set can be re-mirrored. Disk data mirroring is also done for disaster recovery. Entire data is mirrored at remote sites which can then be used for recovery in case of disasters or breakdowns. Data mirroring can be Read More
Group Policy
Group Policy gives users administrative control over people and computers in the user’s network. By using Group Policy, users can define the state of someone’s work environment once, then rely on Windows Server 2003 to continually force the Group Policy settings applied across an entire organization or to specific groups of people and computers. Group Policy Advantages Users can assign group policy in domains, sites, and organizational units. Group policy settings reflect all persons and computers in domain, site, and organizational unit. No one in network has rights to change Read More


Share on: