Wind energy is an alternative source of electricity. This technology harnesses the power of the wind. Specifically, the wind spins turbines which powers generators whose main task is to produce electricity. The wind is one of the safest and cleanest sources of renewable energy today. The concept is similar to those of windmills used for crushing grains or for irrigation. However, in the case of wind turbines, the force of the wind on the blades creates rotational motion; this motion is used to generate electricity. Wind is just a simple Read More
How to Make a Web Page
A webpage is a document written in either XHTML or HTML syntax that is accessed through a web browser. Web pages may include text, images, multimedia files, and links to other web pages or resources on the Internet. Learning how to make a web page using HTML tags in a text editor is necessary to make advanced pages using advanced Web page editors. How to Make a Website Steps to Make a Basic Web Page Step 1 – Open the text editor on your computer. For Windows users, the “Notepad” Read More
Console Cables

The term “console cable” includes a wide variety of cables, all of which can be used to connect various types of computer equipment. The most common type of console cable is the VGA display cable, which includes HDMI and DVI, which connect a computer system to its monitor. Other types of console cables may include the RJ-45 cable, which is used for phone lines, audio and microphone auxiliary cables, which connect speakers or a microphone to a computer, and the popular USB 1.0 and 2.0 cables, which connect USB-based devices Read More
Call Center Solutions
Call centers are usually a centralized location or office where communications over a phone or Internet can either be received or dispatched. Call centers answer or dispatch large amounts of calls. Most call centers are set up for either support services, customer acquisitions, business to business marketing or direct response services, either way, call centers are now part of many businesses large and small to communicate with their present or potential customers. If your company is interested in starting a call center, it is important to look into the different Read More
Make Money on YouTube by Becoming a YouTube Partner

YouTube Partners is a program that YouTube sponsors that allows users to earn revenue on the videos that they upload by placing advertisements within those videos or allowing users to view those videos on a Pay-Per-View basis. YouTube Partners allows users to track which viewers and demographics view their videos and take advantage of numerous copyright protection features within a branded video sharing service. YouTube Partners Requirements YouTube Partners requires that all applicants routinely upload videos that thousands of viewers view and that are ideal for streaming. Also, YouTube Read More
J2SE

J2SE is the Java 2 Standard Edition. J2SE features: Portability JDBC API for database access CORBA technology Java secuity J2SE consists of two components: Core Java and Desktop Java. Core Java provides back-end functionality, while Desktop Java provides GUI (Graphical User Interface) functionality. J2SE contains both the J2SE Development Kit (JDK) and the Java Runtime Environment (JRE). For more information on J2SE, visit J2SE.
How to Create a Windows Vista Boot Disk

In order to create a Windows Vista boot disk, the Windows Vista operating system’s ISO file must be located and downloaded. Microsoft, Dell, and several other computer manufacturers have this file as a downloadable version of the operating system disk, and allows users to create their own disk without having to wait for a physical copy to be sent to them. The file is also available through a number of black market sources on the Internet, specifically in P2P networks and torrent sharing websites. The file can be downloaded directly Read More
Banana Plugs
A banana plug is mainly used to insert speaker wire coming from an amplifier or receiver directly into the speaker. The banana plug is named after its shape. It is a slender, but bulging prong that is similar to a banana. However, unlike bananas, the banana plug is not bent, but straight. Other uses for the banana plug is to test electronic equipment – specifically used to terminate patch cords. It should be noted that the banana plug is the male version and the banana jack is referred to the Read More
How to Burn an ISO Image
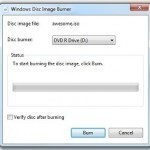
An ISO file contains not only files and folders but also the disk file system metadata. This includes boot code, structures, and attributes. This is why burning an ISO image is different from writing files from a CD or DVD. To burn an ISO image, you need a CD or DVD burning program that can allow you to write on the disk. How to Burn an ISO under Microsoft Windows There are several applications available for disk burning in Windows such as ISO Recorder and Express Burn. The most commonly Read More
Browser Encryption

Browser encryption is a form of cryptography that uses simple encryption algorithms to protect a user’s information while he/she accesses the Internet. While a user may implement virtually any kind of browser related encryption protocol in his/her browser via security plug-ins and add-ons, most forms of browser encryption can already be found in the user’s browser. If a user wishes to have a more secure browser than the one he/she is currently using, he/she could simply download another browser or run a third party application to secure his/her personal information. Read More


Share on: