Four digit security codes protect Kenwood car stereos from theft. If a thief steals a Kenwood car stereo, he/she will not be able to use the stereo until the secret four digit security code is entered. Unfortunately, many legitimate owners are also locked out of their Kenwood car stereos due to these security codes. This typically happens to people who buy used cars from people who forget to share the security code. However, it also happens to people who simply forget their security codes after several years. Common Kenwood Security Read More
Enterprise Resource Planning
Enterprise Resource Planning or ERP is actually a process or approach that attempts to consolidate all of a company’s departments and functions into a single computer system that services each department’s specific needs. It is, in a sense, a convergence of people, hardware, and software into an efficient production, service, and delivery system that creates profit for the company. While the idea is easy to grasp in theory, the reality has been different. Most companies have a conglomeration of different systems and procedures (as well as hardware and software) designed Read More
Ion Propulsion

Ion propulsion refers to a method of space travel in which accelerating ions, rather than traditional chemical rockets, speed up a spacecraft. While ion propulsion produces very little thrust in comparison to chemical propulsion, it produces consistent acceleration that allows the spacecraft to eventually travel faster than a chemical rocket would. Ion propulsion requires an environment with no radical ions, which means that it cannot be used for air travel, and only works well in interplanetary travel due to its exponential acceleration. Ion propulsion also requires a rather large amount Read More
How to Use an iTouch

The iPod Touch is a dumbed down version of the iPhone. It can connect to the Internet, play music, and anything else. However, it cannot be used as a phone. In other words, Apple took their iPhone, removed the phone capabilities and then released the iTouch. With this in mind, using an iTouch is very similar to using an iPhone. Once you get used to the touch screen, it’s very easy. The first thing you need to do to use an iTouch is to plug it into your computer. If Read More
192.168.1.245

Cisco is a leading manufacturer of networking devices such as modems, wireless routers, and network storage devices. Cisco products are sold worldwide to millions of consumers for both residential and commercial purposes. Cisco also markets a number of data plans for some of the largest Internet Service Providers in the world. What is 192.168.1.245? 192.168.1.245 is the default IP address of the control panel found on all Cisco routers and devices. Users can access this control panel by entering 192.168.1.245 into any web browser’s address bar. The user will then Read More
Green Computing
Green computing is the term used to denote efficient use of resources in computing. This term generally relates to the use of computing resources in conjunction with minimizing environmental impact, maximizing economic viability and ensuring social duties. Green computing is very much related to other similar movements like reducing the use of environmentally hazardous materials like CFCs, promoting the use of recyclable materials, minimizing use of non-biodegradable components, and encouraging use of sustainable resources. One of the spin-offs of green computing is EPEAT or Electronic Products Environmental Assessment Tool. EPEAT Read More
How to Solve “McAfee Legacy Programs Must Be Removed First”

McAfee legacy programs are small files that are installed on a computer whenever someone installs a copy of McAfee software, such as McAfee Anti-virus. McAfee legacy programs are intended to help maintain a McAfee program’s current version by automatically updating the software, sending updates about the software’s functionality to McAfee, and performing other small tasks. However, when a user wishes to uninstall McAfee, he/she is required to manually uninstall McAfee legacy programs first. Why do McAfee Legacy Programs Need to Be Removed? McAfee legacy programs need to be removed Read More
How to Delete an Exchange Server Mail Box
Deleting a Microsoft Exchange Server mail box is a relatively simple five step process. However, it is important to note that the mailbox will remain connected for thirty days after deletion. This is called the “mailbox retention period,” during which users can reconnect their mailbox if needed. Deleting a mailbox will not permanently remove it from the server’s database. It will only mark it for future deletion. Once the mailbox retention period expires, the mailbox will be permanently deleted from the database. Someone who does not wish to wait for Read More
How to Use Windows Sound Recorder
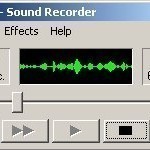
To start Windows Sound Recorder Click the <Start> button Click <All Programs> Click <Accessories> Click <Entertainment> Click <Windows Sound Recorder> Recording a Sound with Windows Sound Recorder To record a sound with Windows Sound Recorder, just press the <Record> button in the lower right corner of the window with a circle icon on it. Playing a Sound with Windows Sound Recorder You can use the <Play> button to play a sound you have just recorded, or you can use <File> and <Open> to play a file stored on your hard Read More
How to Setup Fingerprint Reader on HP Laptops
One of the more interesting pieces of technology that has been released for the laptop computer is the fingerprint reader, which makes logging into a computer so much easier. The software that HP laptops use is Bioscrypt’s VeriSoft Access Manager. By sliding one’s finger across a small metallic sensor, the software is able to read the fingerprint and determine whether that person is authorized to use the computer. If they are, the computer automatically loads up. If not, said person will have to punch a password in. Setting Up the Read More


Share on: