iSCSI stands for Internet SCSI, or Internet Small Computer Systems Interface. iSCSI is the transmission of SCSI commands and data over IP networks, and represents a networking standard for IP-based network data storage. The development of the IETF standard was considered to be the key enabler for expanded usage of storage area networks (SANs) throughout the marketplace. iSCSI technology can be deployed on local or wide area networks through the use of the Internet across distributed resources. How iSCSI Works When an application attempts to read from an iSCSI device, the Read More
Examples of Kinetic Energy

Kinetic energy is the energy of motion. It is also referred to as energy in motion, or as the work required to take an object from being at rest to action/movement. Mathematically, kinetic energy is calculated as ½ of the mass of a body, multiplied by the speed of the body squared, KE=1/2 mv^2. Where Did the Kinetic Energy Term Originate? The term originated with the Greek words kinesis (motion) and energeia (active work). Put together, the two words translate to “Through motion do active work.” More simply, any thing, Read More
How to Convert WMV to MPEG

The Windows Media Video or WMV format is defined by and created by the Microsoft Corporation for playing back video content. The WMV format is part of the Windows Media Framework which has been replaced by the Windows Media Foundation with a greater focus on HD content, streaming technologies, and higher audio and video quality. The WMV format is closely related to the AVI format also created by Microsoft, but is smaller in size and considered more suitable for viewing over an Internet connection. A common task that arises for Read More
What Are RFID Blockers?

RFID (Radio Frequency Identification) is a tracking method that uses RFID tags and readers to determine an item’s exact location within a specific area. RFID is cost effective and does not interfere with the daily routines of customers and employees. Since RFID is so simple, it is widely implemented in retail outlets and grocery stores to prevent theft. RFID is also used to locate employees and prevent unauthorized personnel from entering restricted areas. In order to prevent RFID from working properly, however, many manufacturers have produced “RFID blockers” that are Read More
Converting a Photo to a Pencil Drawing in Photoshop
In order to make a great looking pencil sketch out of a photo, skill and free time are needed to render it by hand or users can take advantage of a tool such as Adobe Photoshop to do the time consuming work in only minutes. Converting a photo into a pencil sketch can be accomplished in just a few steps. First, load the photo into Adobe Photoshop. For this example, a photo of an obsolete camera on a bed sheet will be used. This photo is a random example of Read More
HTML Special Characters

HTML special characters allow us to improve the presentation of our web documents quickly and easily. Description Numeric Alpha Presentation left single quote ‘ ‘ right single quote ’ ’ single low-9 quote ‚ ‚ left double quote “ “ right double quote ” ” double low-9 quote „ „ dagger † † double dagger ‡ ‡ per mill sign ‰ ‰ single left-pointing angle quote ‹ ‹ single right-pointing angle quote › › black spade suit ♠ ♠ black club suit ♣ ♣ black heart suit ♥ ♥ black Read More
How to Remove Mirar

Mirar is also referred to as Getmirar. It is a spyware application, which means it can endanger the security and stability of your machine and access the private files or confidential information stored in it. Spyware applications such as Mirar send out advertisements depending on the current URLs of the Internet browser. Mirar is capable of installing itself as a internet browser add-on. It drops registry entries in the System Registry in order for the OS to validate its authenticity as a internet browser add-on. In order to remove Mirar Read More
What is a Windows OEM?

OEM (Original Equipment Manufacturer) is one of the terms used to describe products that come directly from the manufacturer. This applies to both hardware and software designed to be used on a computer system. Microsoft’s Windows Operating System with OEM license is available for purchase. OEM versions of Windows function just like any other Windows installation. They are designed for PC producers and System Builders who resell the final product. Home users and computer hobbyists are technically not allowed to install Windows OS with OEM license. Windows OEM does not Read More
How to Use Audacity

Audacity is a free recording program designed with the user’s needs in mind. Unlike other programs, Audacity includes a wide assortment of tools and features that allow the user to record, manipulate, and share audio files. Audacity creates digital sound files from a number of sources including cassette tapes, vinyl records, minidisks, and even streaming audio with the proper software. Although Audacity can produce CDs and work with a number of audio files, it is first and foremost an audio editing software. Audacity is a completely open source and free Read More
Graphs
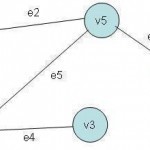
A graph is an important non linear data structure. This data structure is used to represent relationship between pairs of elements, which may not, necessarily, be hierarchical in nature. A graph is defined as: “Graph G is an ordered set (V, E), where V(G) represents the set of elements, called vertices, and E(G) represents the edges between these vertices.” Graphs can be of either type, Undirected Graph Directed Graph Figures below show sample graphs. V(G) = { v1, v2, v3, v4, v5 } E(G) = { e1, e2, e3, e4, Read More


Share on: