What are Service Packs and Hotfixes Service packs and hotfixes are network updates that need to be applied to network computers. Hotfixes are also sometimes referred to as security hotfixes or security fixes. Before delving into the differences between service packs, and hotfixes; you can think of a service pack as being a collection of updates, or large executable files that relate to an Operating System (OS), and a hotfix as being one or multiple files that are applied to the OS to fix a specific critical problem. Service packs Read More
How to Fix Windows Search
Windows Search (Windows Instant) is a program in the Windows Operating System that allows users to search for specific files, folders, or other remnants of data on one or more hard drives or some other storage device. It allows users to search for customized keywords, specify storage locations, browse for files, and toggle through a multitude of functions. Windows Search is very easy to use, can find virtually any type of file on the user’s hard drive (including emails and data files), and supports natural language, allowing users to enter Read More
Pointing Devices

A pointing device is any piece of hardware that is used to allow a user to input spatial data to a computer. By moving a mouse, pen or a finger around, a user can implement movements and changes on the computer screen. The most common type of pointing device is the mouse and the arrow. When the mouse is moved on a mouse pad, the arrow on the screen moves. When the user clicks down on the mouse, the arrow clicks on the object it is hovering over. There are Read More
Restricted Shells
A restricted shell is a Unix shell that has been modified to allow the Unix shell user to do fewer things than a normal shell would allow him to do. It may allow the user to run only certain programs. It may stop the user from changing directories. Many sites run their own restricted shells to allow limited use of their systems over the Internet. Restricted shells often make use of the restricted shell (rsh). On poorly implemented restricted shells, the shell user can break out of the restricted environment Read More
Full Backup
A full backup is a backup of every file on a file system, whether that file has changed or not. The alternatives to a full backup are incremental backup and differential backup. A full backup takes longer to accomplish and requires the most storage space on the backup media, but it also provides the quickest restore times. A full backup should be performed weekly or monthly on production systems, along with daily differential backups. It would be best to build full backups at all time, since they are the most Read More
Insertion Sort
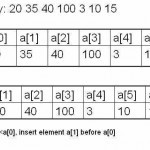
This algorithm is very popular with bridge players when they sort their cards. In this procedure, we pick up a particular value and then insert it at the appropriate place in the sorted sub list. This algorithm requires n-1 passes. Pass1: a[1] is inserted either before or after a[0] so that a[0] and a[1] are sorted. Pass2: a[2] is inserted either before a[0] or between a[0] and a[1] or after a[1] so that the elements a[0], a[1], a[2] are sorted. Pass3: a[3] is inserted either before a[0] or between a[0] Read More
How Does a Blackberry Work?
A BlackBerry is a popular mobile phone that Research in Motion (RIM) produced. It is able to send and receive email, download and update calendars, and make phone calls. Unlike other phones, the BlackBerry comes with a complete, alphanumeric keypad in order to support the email function that has made the phone so popular in business and academic circles. How Does a BlackBerry Receive Email? BlackBerry phones typically receive email via the BlackBerry Exchange mail service. The BlackBerry redirector checks the email account and forwards it to the BlackBerry device Read More
How to Delete Duplicate Songs in iTunes
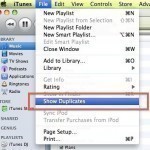
iTunes is a popular free digital media application provided by Apple for use on the iPhone, iPad, iPod, Mac and PCs. After being used for a significant amount of time users may accrue a large number of songs in the iTunes library, increasing the chances that some of them may be duplicates. Finding and deleting duplicate songs may save a significant amount of space, depending on how many duplicate songs exist. How to Consolidate the iTunes Music Library If users have only purchased music through the iTunes or Amazon music Read More
How Was the Earth Formed

As science is beginning to move towards terraforming, a process that converts a “dead” planet into a thriving environment for life, the question of “How was the Earth formed?” comes to mind. Unfortunately, there is no exact answer when it comes to the formation of the Earth as no one was around back then to record it. Religion claims that God created the Earth in seven days several thousand years ago while science says that evolution, natural selection, and physics created the Earth billions of years ago. As religious claims Read More
Connection Manager
Connection Manager is versatile client dialer and connection software that you can customize by using the Connection Manager Administration Kit (CMAK) wizard. The CMAK wizard provides defaults that support quick and easy creation of a basic Connection Manager service profile. If you want to use all of the defaults and do not want to take advantage of the many customizable elements, you probably do not need this documentation. However, if you want a custom dialer that promotes your brand and supports more advanced functions, such as automatic phone book updates Read More


Share on: