Determining Security Business Requirements When analyzing and determining the security business requirements of the organization, you have to include the following factors: Business model: The business model that the organization uses greatly influences the type of security an organization implements. An organization that has world-wide branches would have different security requirements to a business that has a single office. Business processes: To successfully implement security, you have to know how business processes within the organization work. You have to ensure that security does not prevent business processes from being carried Read More
Implementing Public Key Infrastructure
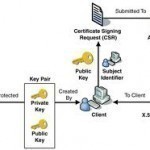
An Overview on the Public Key Infrastructure (PKI) A set of components, standards, and protocols make up the Public Key Infrastructure (PKI), which protects data as it is transmitted over the network. The PKI is an integral aspect of security within a network. Digital certificates form the basis of the PKI because these certificates use cryptographic algorithms and key lengths to protect data as it is transmitted over the network. The more important components of the PKI are summarized below: Cryptographic components are the encryption and hashing algorithms that are Read More
Implementing Auditing
Auditing Overview Auditing enables you to determine which activities are occurring on your system and allows you to track access to objects, files and folders; and modifications made to the objects, files and folders. Auditing also enables you to collect information associated with resource access and usage on your system by allowing you to audit system logon, file access, and object access. Security auditing events are written to the Security log of the system and can be accessed from the Event Viewer tool. Because event logs grow over time and Read More
Task Manager Has Been Disabled By Your Administrator
Computer malware has evolved at a rapid rate in recent years. A common trend among the fake anti-virus programs that the Trojan virus deploys on the Internet is disabling the computer’s Task Manager. The associated virus does this in order to make it more difficult to remove infections from computers. When this happens to a computer, the registry editor must be used to remove the malware. Depending on the nature of the computer infection and the configuration of the Windows computer, several methods can be used to repair the problem. Read More
Implementing Internet Connections

E-mail and Web sites have evolved into being important mechanisms for a vast number of organizations. Internet connectivity or connections support a company’s business in a number of ways. Company employees use the Internet to exchange e-mail with other employees at different branch offices, and with business partners and suppliers; to access the LAN when working from home; to conduct research using the Web; and mobile users utilize the Internet to remotely access the LAN. Each organization would have different requirements when it comes to Internet connections. Some organizations might Read More
How to Add a User to Windows
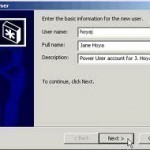
The procedure for adding a new user to Windows depends on the Microsoft Windows version. In addition, there are several ways to add new users to most Windows versions. The instructions presented here show only a few of the possible paths to creating new users on Windows. Add a User to Windows XP Click the Start button Click the Control Panel menu item Double-click the User Accounts icon Click the Create a new account menu item Type a name for the new account in the data entry box Click the Read More
Defining a Baseline Security Template
Security Templates Review A security template is collection of security configuration settings that can be applied to a domain controller, member server or a workstation. The settings within a security template control the security configuration of a computer through both local policies and group policies. A security template can be applied to a local computer, or incorporated into a Group Policy object in Active Directory. You can manage one computer or multiple computers through the security settings contained within a security template. For computers that do not belong to an Read More
Securing Domain Controllers
Domain Controllers Security Issues When it comes to Windows Server 2003 Active Directory networks, one of the most important server roles which can be configured is probably the domain controllers role. Domain controllers perform a number of important functions and control activities within a domain, including the following: Contain a replica of the Active Directory directory for the domain to which it belongs, and is responsible for managing that directory Provide authentication services for the network. Store and distribute group policies. Manage access to network resources within the domain. Manage Read More
Understanding Certificate Authorities
An Overview on Certificate Authorities In the Public Key Infrastructure (PKI), digital certificates are based on public key cryptography. The PKI consists of a set of components, policies, protocols, and technologies that provide data authentication, integrity, and confidentiality through the use of certificates, and public and private keys. Data is protected by applying a hashing algorithm and signature algorithm to the original message. A hashing algorithm is an intricate mathematical algorithm which is applied to the message. The hashing algorithms which are commonly used are MD2, MD4, MD5, and SHA-1. Read More
Securing File and Print Servers
The file server role stores data for network users, and provides access to users for files stored on the file server. File servers enable users to store files in a centralized location and share files with another user. The print server role provides network printing capabilities for the network. Through the print server role, you can configure a server to manage printing functions on the network. The print server is the computer where the print drivers are located that manage printing between printers and client computers. The print servers also Read More


Share on: