Windows registry The Windows Registry is a focal database that holds all the settings pertaining to Windows operating systems. It includes data and settings for hardware, software, and user related information. Any change made to the system in terms of system settings, hardware or software is reflected in the Windows registry. The Windows registry can be used to view runtime information about active hardware and software, and it can also be used for troubleshooting and fixing Windows issues. However only advanced users can view and edit settings in the registry, Read More
Group Policy
Group Policy gives users administrative control over people and computers in the user’s network. By using Group Policy, users can define the state of someone’s work environment once, then rely on Windows Server 2003 to continually force the Group Policy settings applied across an entire organization or to specific groups of people and computers. Group Policy Advantages Users can assign group policy in domains, sites, and organizational units. Group policy settings reflect all persons and computers in domain, site, and organizational unit. No one in network has rights to change Read More
How to Change the Windows Toolbar
The toolbar is a component of the Graphical User Interface (GUI) that houses various input and output components such as buttons, menus, icons and so on. End-users can customize toolbars as per their personal requirements. Toolbars can be found in operating systems, software applications, and web browsers. The latest development in toolbar interfacing is the ribbon interface. It basically places groups of toolbars within tabs. The Windows operating system utilizes toolbars in different areas of its GUI. Several of its applications and tools such as Microsoft Office Suite, Internet Explorer, Read More
Understanding Internet Security and Acceleration Server (ISA Server)
Internet Security and Acceleration Server (ISA Server) Overview Microsoft Internet Security and Acceleration Server (ISA Server) is combination of a firewall and Web caching server that can be used to protect the enterprise from external access, while sharing a internet connection on the network. The multilayer firewall of ISA Server protects valuable network resources of the enterprise from unauthorized external access, attacks from hackers, and malicious viruses. You can also control client access to the Internet. The Web cache server enables faster Web access for users by serving objects locally Read More
Implementing IAS
Internet Authentication Service (IAS) Overview In most organizations that have multiple network access servers, the centralization of authentication and accounting of connections being established at a centralized server is the better approach than each network access server performing authentication and accounting services. The Remote Authentication Dial-In User Service (RADIUS) protocol is the recognized protocol for providing a centralized authentication, accounting, authentication and authorization for remote network access. RADIUS is a internet Engineering Task Force (IETF) standard. Essentially, the RADIUS protocol can be used to control access for dial-up networks, VPNs Read More
How to Open PPS Files
PPS, or PowerPoint, files are files that are created using either PowerPoint or a similar program. PowerPoint is a program that ships with Microsoft Office and allows users to create fully-functional presentations and slideshows for use in schools, meetings, and lectures. While PowerPoint itself is a great program, some users do not appreciate the Microsoft Office layout or the price tag that accompanies it. For these reasons, a large number of similar programs have been introduced to the market since the release of PowerPoint that provide either the same or Read More
How to Fix Internal Error 2753
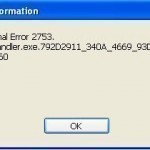
Internal Error 2753 refers to a problem associated with Windows Installer that prevents programs from being installed on a computer. Internal Error 2753 may be displayed through a number of programs and can cause the user a great amount of distress when trying to install a new software. While Internal Error 2753 can be difficult to repair, causing many users to reinstall their entire operating system, it can be fixed via the Windows DOS Command Prompt. What is Windows Installer? Windows Installer is a software that Windows provides. It is Read More
mom.exe
MOM.exe is a monitoring program for the Catalyst Control Center that ATI Technologies created. It monitors ATI video card graphics use and is essential for running certain functions of the video card’s graphics driver. MOM.exe is included with all drivers and updates for version 7.2 and newer of the Catalyst Control Center and generally runs in the computer’s background. While MOM.exe may display error messages, it is not a part of the Windows Registry, can be easily removed, and does not pose any threat to computers. Spyware While MOM.exe Read More
How to Kill a Process in Windows
Computer programs or applications commonly have one or more processes that are executing to support the program. These processes are instances of the running application and may have one or many Operating System threads dedicated to receive computer resources. Each program thread may execute any portion of the process code depending on the program design. Unfortunately, some programs will have a process hang or freeze and will not allow the end user to kill the process from the Windows Task Manager. If you attempt to close a process by selecting Read More
DHCP and Remote Access
DHCP and Remote Access Overview When a remote computer connects to a remote access server (RRAS), it is automatically provided with an IP address when the Point-to-Point Protocol (PPP) connection is established. You can configure the RRAS server to allocate IP addresses to remote clients from: A static range of IP addresses: This method is usually implemented when there are no internal DHCP servers. An existing DHCP Server: This is achieved by relaying clients to the DHCP server for IP address allocation. If you have an internal DHCP server, you Read More


Share on: