A DASD, or Direct Access Storage Disk, is a type of storage device that is connected directly to a user’s computer rather than being connected to the network. Because many types of storage device connect directly to a user’s computer, the term “DASD” may apply to a variety of different devices; however, a DASD is typically a storage device that contains a significant amount of memory and a relatively low access time. For example, desktop servers and external hard drives are good examples of DASDs, although flash drives and SD Read More
Projector Lumens

Projectors have quite a variety of uses these days, whether in the boardroom or classroom to give a presentation, or the home to project digital, high definition TV and video to a screen. While there are many aspects that determine whether a projector will project high quality images (e.g. resolution, contrast, etc.), one type of measurement that users should be aware of is Lumens. What are Lumens? Lumens are a unit of measurement of the total brightness that comes from a light source, in this case, a projector. One may Read More
How to Backup iTunes
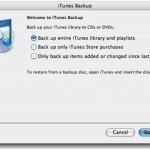
Since the release of iTunes in 2001, a significant number of computer users have used the proprietary application as their primary means of managing multimedia files on their computer. Unfortunately, there is no inherent redundancy built into the iTunes program to help guard against computer hard drive failure, significant malware infection, etc. As a result, most iTunes users have to backup iTunes after their music and movie library have grown to a significant size. Before backing up iTunes, however, you will need to consolidate your iTunes library. How to Consolidate Read More
Daylight Savings Time

Daylight Savings time, or Daylight Saving Time, is the process of adjusting the clocks twice a year to add more daylight time in the afternoons and less in the mornings. Daylight Savings Time has undergone many changes and thrown under much controversy in its history but it remains a vital part of our society today, all around the world. In this article, we will go over how Daylight Savings Time started, how it works, the pros and cons, and how Daylight Savings Time effects computers. Origins and History Daylight Savings Read More
Understanding Active Directory
The Limitations of the Windows NT Domain Model and Network Security With Windows NT, domains were utilized to manage users, and to manage and secure network resources. A domain is the logical grouping of servers and network resources under a single domain name. In Windows NT, a domain could be considered as a central database containing security information which was then basically used to manage users and network resources. The Windows NT computers operated as domain controllers, with each domain essentially having one Primary Domain Controller (PDC) and one or Read More
How to Repair a Broken Hard Disk

Broken hard disks can be both a nuisance and a major loss to business and personal affairs whenever files are lost or inaccessible. Fortunately, there are several things users can do to repair a broken hard disk before throwing it out in order to restore lost or inaccessible files. Let the Hard Disk Cool Down The first thing users should do is allow their hard disk to cool down by shutting the computer off and unplugging it from the wall. The user can cool his/her hard disk down faster Read More
How to Access Wireless Router Settings

What is a Wireless Router? A wireless router is a device that wirelessly connects multiple computers and devices to the Internet. Wireless routers’ design and capabilities vary and they drastically range in price, but are used for the same function. Wireless routers are usually very easy to setup and many provide the user with built-in security methods such as data encryption or a firewall. As a result, wireless routers allow users to easily setup a wireless network that all of the computers and devices in a home, office, or other Read More
How to Turn Off Your Computer in Vista
Turning off your computer in Vista can be a bit tricky because Vista doesn't show you a "Turn off computer" button. So when you want to turn off your computer, here are four simple options: Method 1 Start up your computer. Click on the power button in the Start menu. If you see a yellow exclamation point on the power button that means Vista will install updates before it turns your computer off. Method 2 Lock your computer Click on the lock button in the Start menu. To be able Read More
ISDN (Integrated Services Digital Network)
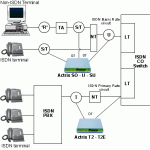
ISDN (Integrated Services Digital Network) is a system of digital phone connections that has been designed for sending voice, video, and data simultaneously over digital or ordinary phone lines, with a much faster speed and higher quality than an analog system can provide. ISDN is basically a set of protocol for making and breaking circuit switched connections as well as for advanced call features for the customers. ISDN is the international communication standard for data transmission along telephone lines and has transmission speeds up to 64 Kbps per channel. The Read More
Routing

Routing is the process of moving packets through an internetwork, such as the Internet. Routing actually consists of two separate, but related, tasks: Defining paths for the transmission of packets through an internetwork. Forwarding packets based upon the defined paths. Routing takes place in IP networks, based on IP routing tables and its entries. The information in the IP routing tables is used by IP hosts to transfer data over the internetwork. Routers are devices operating at the network layer of the OSI model that use the IP routing tables to forward Read More


Share on: