Over the years there have been many versions of DOS, including PC-DOS, MS-DOS, DR-DOS, and 4DOS. Although DOS is not used frequently any more, the DOS commands are still available in the Microsoft Windows XP command shell. Listed below are the commands for the DOS command shell included with Microsoft Windows XP. DOS Commands ASSOC Displays or modifies file extension associations Syntax ASSOC [.ext[=[fileType]]] .ext – Specifies the file extension to associate the file type with fileType – Specifies the file type to associate with the file extension Type ASSOC Read More
Understanding the IPX-SPX Protocol
IPX/SPX is a protocol suite that is implemented on many corporate internetworks. IPX/SPX was developed to operate in Novell Netware in LAN environment. But today, the IPX/SPX is also used in Microsoft NT, Microsoft XP and Lotus Notes environment along with Vista. IPX/SPX on Cisco IOS The Cisco IOS also provides a wide range of configuration tools and options for IPX/SPX protocol suite. The Cisco IPX/SPX router configuration tools are very much similar with Cisco IP router configuration. Some of them are listed: The Cisco IOS provides static route support Read More
How to Use the Windows XP Recovery Console
The Windows XP Recovery Console can be used to repair problems which prevent a Windows XP system from booting. Boot Windows XP from CD or Floppy First, boot the computer from the Microsoft Windows XP CD. Before you start the process, go into your BIOS settings and ensure that your CD-ROM drive has the highest drive priority and not the disk drive or some other drive. If you don’t have a Microsoft Windows XP CD, or if the computer you are working on does not have a CD drive, you Read More
How to Change Your Windows Password
Whether you want to change the password on your own computer at home, office computer, or a computer that’s networked with other users, you can easily customize your Windows settings to protect specific files and folders from others either viewing or editing them. Creating or changing the windows password is very simple. It should be noted that changing your password on Windows will differ, depending on whether you are on a stand alone computer or a computer that is connected to a network domain (workgroup). Change your Windows password on Read More
Water-Based Bomb Inhibitors

Water-based bomb inhibitors are water-filled devices that are used to attenuate or weaken the effects of a bomb blast. Water is used as a bomb inhibitor for these devices as water has a relatively high mass and is relatively available in almost any area. Water-based bomb inhibitors are successful in reducing blast and fragmentation by 90%. They also eliminate the risk of fire, reduce loss of property as well as casualty incidence. Furthermore, it preserves forensic evidence. It’s easy to install, too. Bomb inhibitors are gaining popularity all over the Read More
Ethernet at the Physical Layer
Ethernet is the most popular Local Area Network architecture that was jointly developed by Digital Equipment Corporation, Intel Corporation and Xerox Corporation. It consists of certain specifications and standards as well as hardware devices and components. Ethernet provides services corresponding to physical layer and data link layer of the OSI reference model. Each Ethernet physical layer protocol has a three part name that summarizes its characteristics. The components specified in the naming convention correspond to LAN speed, signaling method, and physical media type. The following table summarizes the differences between Read More
Data Governance
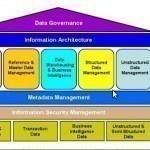
Data governance is a discipline found within the workforce where there is a grouping of data quality and management, risk management and business process management when dealing with the handling of data found in an organization. The ultimate goal with data governance is to have control — ideally positively — over the data in the organization. Specifically, they want to control the processes and methods in which the data is handled by their data stewards. The fundamental purpose of data governance, as described above, is to somehow mesh all the Read More
802.1X
802.1X is an IEEE standard for EAP encapsulation over wired or wireless Ethernet. 802.1X is also known as EAPoL (EAP over LAN). This only makes sense when you recall that EAP was originally designed for use over PPP. 802.1X Roles 802.1X defines three roles: Name Description Supplicant User or client requesting authentication Authentication Server The server providing authentication Authenticator The device which the Supplicant requests access to, and which requests access from the Authentication Server. 802.1X and RSN 802.1X is particularly well suited for wireless LAN applications because it requires Read More
DisplayPort
DisplayPort is the new digital display interface standard. It has been recently approved (5/2006) by VESA and will be hitting the markets in 2008. For most computer users, the fairly big and bulky VGA port is familiar. While the VGA port has been extremely reliable and has delivered competent performance, the new standard – the Display Port – is considered to be quite an upgrade from traditional VGA ports and is on par with HDMI. The DisplayPort will be mainly manufactured by large computer makers to send video, as well Read More
Iterations
An Iteration involves repeating some portion of a program, a specified number of time or until a particular condition is satisfied. This repetitive operation in C and C++ is achieved through for, while and do–while loop. How does a for loop work? A for loop is the easiest iteration loop to understand the C and C++ loops. All the loop elements are gathered at one place unlike the other loops, where, the loop elements are scattered all over the loop body. Syntax: for( initialization ; condition ; increment or decrement Read More


Share on: