3GP is the standard used today on the 3G mobile phones. It is distinguished in two different standards; the 3GPP, which is used on GSM-based phones and have the file extension, .3gp. There is also the 3GPP2, which is for CDMA-based phones, and have the file extension .3g2. These two standards are MPEG-4 and H.263 based while having an AAC and an AMR audio. This multimedia container format was defined by the Third Generation Partnership Project (3GPP), a group of telecommunications partners, the ETSI from Europe, ARIB/TTC from Japan, TTA Read More
Computer Privacy Screen
Computer privacy screens, sometimes called computer privacy filters offers added security by making any image on the screen visible only to the computer user sitting directly in front of the image. Other angles that are not in direct view of the screen are distorted or blacked out completely. Types of Computer Privacy Screens There are three main types of computer privacy screens, they include; CRT (cathode ray tube) monitor privacy screens, LCD monitor privacy screens and laptop monitor privacy screens. Computer Privacy Screens Fabric and Installation In general, computer privacy Read More
Accelerating Internet Connectivity through the ISA Server Cache
ISA Server Cache Summary The Web Proxy service of ISA Server enables frequently requested Web objects to be cached. Subsequent client requests are checked against the ISA Server cache to determine whether they can be served from the cache. A new request is initiated if the ISA Server cache cannot be utilized to serve the client request. ISA Server stores most frequently accessed items in RAM. The items are then retrieved from memory instead of from disk. Objects remain in the ISA Server cache until either of the following events Read More
Subnet Masks
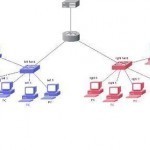
A subnet mask allows users to identify which part of an IP address is reserved for the network and which part is available for host use. By looking at the IP address alone, especially now with classless inter-domain routing, users cannot tell which part of the address is which. Adding the subnet mask or netmask gives users all the information needed to calculate network and host portions of the address with ease. In summary, knowing the subnet mask can allow users to easily calculate whether IP addresses are on the Read More
Speedometer Calibration
One of the most prominent gauges on an automobile’s dashboard is the speedometer. Its primary function is to give a visual indication of a vehicle’s speed in miles or kilometers (or both) per hour. Since the majority of these devices are still analog, they may require speedometer calibration when new tires are installed, major automotive repair work is completed, or it gives incorrect readings on a consistent basis. When Were Speedometers First Used? Automobile manufacturers first included Speedometers as standard equipment in 1910 as the need to limit drivers’ speeds Read More
iDEN (Integrated Digital Enhanced Network)

An IDEN, or Integrated Dispatch Enhanced Network, is a radio service provided by some mobile telephones that allows subscribers to talk to nearby subscribers who have similar phones without dialing their individual numbers. IDENs are often provided as a free service on modern mobile phones, such as Nextel, or as a premium service that can be activated, such as on SouthernLINC phones. IDENs are technically able to support communications up to 6 miles in all directions, but have a practical limit of 1-2 miles due to interference from buildings and Read More
Understanding and Implementing Access Control
An Overview of Access Control Allowing users and computers unlimited access to system resources and network resources can ultimately compromise the security and stability of an organization. Even though users and computers need to access network and system resources to perform certain tasks, the access that they require should be limited to those necessary to perform these tasks. Access control has since evolved from being access oriented with Windows 2000 and earlier to being control oriented with Windows Server 2003. With the launch of Windows Server 2003, Microsoft tightened its Read More
Galvanic Corrosion

Galvanic corrosion occurs when two dissimilar alloys or metals come in contact with each other in a corrosive, conducting environment. When they touch, the anode metal corrodes faster than it would when submersed in the solution and the cathode metal corrodes much slower. Galvanic corrosion is not considered a bad quality, however, as the concept is commonly used in industry to protect more expensive metals by allowing less expensive ones to serve as anodes and be worn down instead. Why does Galvanic Corrosion Occur? When an electrolyte exists between two Read More
How Do I Locate Public Domain Books?
Once intellectual property enters the public domain, it is not longer protected by international copyright law and may be reused for free. When a book enters the public domain, it is normally due to the copyright term of the work expiring, the work being created as a product of government employment, or the creator of the work failing to complete the copyright requirements in his or her country. Authors of books classically have the rights to reproduce, create derivative works, and display the book or work that has been created. Read More
How to Embed Flash
Flash, or Adobe Flash, is a type of video file that can be embedded into webpages in order to display animations and/or provide interactivity for the user. Flash is often used in games, interactive office programs, and advertisements. Flash is relatively easy to use and can be generated by a number of websites and programs that are specifically designed for creating Flash video files. These services also often provide embedding options that allow the user to designate a location and embed the file to a website, blog, or profile with Read More


Share on: