If you are unable to repair a corrupt database that has been caused by a system failure, a virus attach, a power failure, or a similar disaster, you can first delete the WINS database and then entirely restore it from a backup. The WINS management console is a comprehensive tool which can be used to plan and perform a WINS database backup. Once the database backup directory has been specified, by default, WINS takes complete backup after every 24 hours and stores it in that directory. The WINS management console Read More
Networking Tutorials
Networking Tutorials Learn the terminologies, and the basics on Networking. Here, you will learn the purpose of designing a network, devices used in networking, network design, network management and a lot more! Open System Interconnection Model The Open System Interconnection Reference Model is used to detail the description for layered communications in computer networks. It is also used for the purpose of designing computer network protocols. This model, which was developed as part of the ISO’s Open System Interconnection initiative to standardize the networking arena, consists of seven layers. This Read More
SMS Database Maintenance and Disaster Recovery
SMS Database Maintenance Tasks The main SMS database maintenance task that you need to perform is to implement a backup strategy for the SMS site server and SMS database server. A backup is the process of archiving data and system files on a computer to a different location on a hard disk, or other media type. A backup plan or strategy should detail the data that has to be backed up, the manner in which the data should be backed up, the frequency at which the backups should occur, and Read More
Hot Water Circulators
A hot water circulator (circulator pump) is a device that circulates hot water through a house’s pipes so that hot water is always instantly available. In traditional one-way plumbing systems, water is run through a hot water heater and directed through the pipes towards the taps whenever a tap is turned on. When a tap is off, the water remaining in the pipes begins to cool and becomes stagnant. This is why users often have to wait a few seconds for the water to get hot. In a plumbing system Read More
SCTP (Stream Control Transmission Protocol)
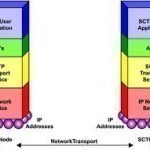
The Stream Control Transmission Protocol (SCTP) is a reliable transport protocol that works on a connectionless IP packet network. It transports Public Switched Telephone Network (PSTN) messages over networks and also has other functions. SCTP was created in order to correct the TCP’s shortcomings, while carrying real-time signaling information over a network. It also runs on top of the UDP network layer if and when required. Services that SCTP Offers The SCTP offers the following services: Fragments data to the discovered path MTU size. Transfers Error free, non-duplicated user data that Read More
IC Layout
When dealing with IC design, it is important to have a solid integrated circuit layout. An IC layout is the use of different geometric shapes to correspond with the patterns of metal, oxide or semiconductor layers that are the building blocks of the components found in an integrated circuit. Other names that IC layout has are IC mask layout and mask design. When there are so many different components that an engineer needs to consider, it is important for the geometric shapes to be connected properly. There are many interactions Read More
What is a BUC?

A BUC (Block Upconverter) is a device that converts radio signals from a lower frequency to a higher frequency. BUCs are used in satellite uplink transmissions in order to transfer data from a ground based unit to a satellite in orbit that will then be redirected to another ground based unit in separate location. Likewise, BUCs are used in long distance communication between two or more ground based radio towers. BUCs are often found in communication broadcast systems for television and Internet access, weather systems, and government agencies. How a Read More
Personal Firewall
A personal firewall is a firewall-like software application which runs on a users PC. Traditional software-based firewalls run as the only application on stand-alone computers which have been hardened to protect against hackers. Personal firewalls run on PC’s along with all of the other applications required by the PC user. Traditional firewalls protect entire networks. Personal firewalls are normally designed to protect only the PC upon which they are installed. Because they run on the same computer as the other applications, personal firewalls have more information available to them than Read More
CDMA-2000 1xRTT
CDMA-2000 1xRTT is a 3G wireless technology based on the CDMA platform. The 1x in 1xRTT refers to 1x the number of 1.25MHz channels. The RTT in 1xRTT stands for Radio Transmission Technology. The CDMA-2000 1xRTT protocol was developed by Qualcomm. CDMA-2000 1xRTT is a CDMA version of the IMT-2000 standard which was developed by the International Telecommunication Union (ITU). Verizon and Sprint both operate CDMA-2000 1xRTT services in the United States. CDMA-2000 1xRTT Specifications Fixed/Mobile Mobile Circuit/Packet Packet Max Bandwidth 144Kb Range Coverage area of host network Frequency Frequency Read More
What is Installous?

Installous is an installation package for jailbroken iPhones, iPads, iPods, and other Apple devices that allow users to install “illegal” applications. Illegal applications refer to unofficial applications and those that other Apple users have cracked. This means that Installous previews Apple applications before they are purchased. Installous is free and can be downloaded via Cydia, the online database of portable device applications. The use of Installous and similar programs is commonly referred to as “jailbreaking” and although it was once considered unlawful, it is now perfectly legal. However, there are Read More


Share on: