Convert Feet to Meters Automatically To convert Feet to Meters, enter the number of feet to be converted into the feet box below. Feet: Feet (ft) Results: Micrometers (µm) 0 Millimeters (mm) 0 Centimeters (cm) 0 Meters (m) 0 Kilometers (km) 0 Inches (in) 0 Yards (yd) 0 Rods (rd) 0 Miles (mi) 0 Convert Feet to Meters Manually This chart allows users to convert Feet to Meters manually. For example, the chart below shows that 8 feet is equal to 2.438 meters. Feet Meters 1 0.305 2 0.610 3 Read More
How to Remove a Fake Windows Security Alert
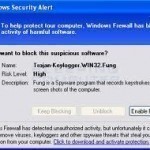
A fake security alert is an event that some types of viruses and other malicious software generate to make a computer appear to be infected with viruses. Fake anti-virus software cause these fake security alerts. Such fake anti-virus software pretend to scan a computer for malicious software and then displays a long list of “infections” that are really essential computer files, application files, or files that do not even exist. When the user attempts to remove these infections with the fake anti-virus software, the program tells him/her to upgrade to Read More
ISAKMP
ISAKMP (Internet Security Association and Key Management Protocol) is a protocol for establishing Security Associations (SA) and cryptographic keys in a internet environment. ISAKMP defines the procedures for authenticating a communicating peer, creation and management of Security Associations, key generation techniques, and threat mitigation (e.g. denial of service and replay attacks). ISAKMP typically utilizes IKE for key exchange, although other methods can be implemented. ISAKMP is documented in RFC 2048: Internet Security Association and Key Management Protocol (ISAKMP). ISAKMP under IP (Internet Protocol) is documented in RFC 2407: The Internet Read More
How to Change WEP to WPA

Changing WEP to WPA is a great way to increase a wireless network’s security. These are the two main types of protection available through modern wireless routers: WEP or Wired Equivalent Privacy is a security algorithm that wireless networks use. Hackers can break into wireless networks using WEP very easily with simple software that is readily available online. WPA or Wi-Fi Protected Access is a special certification program that offers a security protocol that makes it much more difficult to break into the network. This security increase is often much Read More
How to Share Your Calendar in Outlook
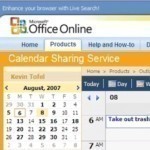
If you are using Microsoft Outlook 2003, you can give permissions for others to view your calendar. On the Calendar button, click Share My Calendar link. Then click on the Permissions tab. To the right of that you will see and Add button. Click the Add button. Add the name of the person who you want to be able to read your calendar. Then click OK. Now in the box in the middle, select the person you want to give permission to by clicking their name. This will highlight it. Read More
1024×768
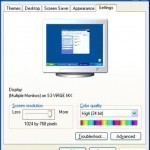
1024×768 is one of the most popular resolutions for PC video screens. The 1024×768 resolution was introduced as an enhancement to the Super VGA (SVGA) standard. 1024 is the horizontal resolution and represents the number of columns supported by the video card and monitor; 768 is the vertical resolution and represents the number of rows (or lines) supported. 1024×768 on the Web 1024×768 was the most popular screen resolution in use by our site visitors for many years. As of 2012, the wider 1366×768 resolution has taken the top spot Read More
How Does an Alternator Work?
Modern technology has presented society with many tools and luxuries that make the lives of billions of people easier on a daily basis. One of these luxuries is the automobile. With its gasoline compression, electrical conversions, and ability to move at very fast speeds, the automobile can get its driver across the country in a matter of hours. Unfortunately, there is a limit to the automobile's capacity to maintain its electrical power. To correct this issue, scientists and manufacturers have invented the alternator. This article will explore what an alternator Read More
Active Directory Terminology and Concepts
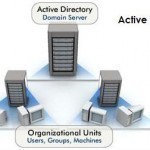
The Active Directory data store (directory) is the database that holds all directory information such as information on users, computer, groups, other objects, and the objects that users can access. It also includes other network components. The Active Directory data store is stored on the server’s hard disk by means of the Ntds.dit file. The file has to be stored on a drive that is formatted with the NTFS file system. The Ntds.dit file is placed in the Ntds folder in the systemroot. When changes are made to the directory, Read More
Deleting an Element from a Doubly Linked List

To delete an element from the list, first the pointers are set properly and then the memory occupied by the node to be deleted is deallocated (freed). Deletion in the list can take place at the following positions. At the beginning of the list At the end of the list After a given element Before a given element Deleting from the Beginning of the List An element from the beginning of the list can be deleted by performing the following steps: Assign the value of head (address of the first Read More
AIM Express
For many, AIM Express presents the next generation of instant messaging services. Unlike most instant messenger programs, AIM Express does not require users to download any software. This means you can use AIM Express at locations other than your home computer. How does AIM Express work? AIM Express uses your browser window, rather than a software package, to run. Anyone who has an AOL or AIM screen name can log into AIM Express. The browser will pull up a separate window that contains the type of information you would associate Read More


Share on: