Batteries are used constantly by the public, from cars, computers, laptops, radios, to portable MP3 players, cell phones, and clocks. A battery, in a nut shell, can be defined as a can filled with certain chemicals that produce electrons from electrochemical reactions. Alessandro Volta created the first battery in 1800. In order to accomplish his motives, he stacked layers of zinc, blotting paper soaked in salt water, and silver. He alternated the layers, making sure the top and bottom layers were different metals. With a wire attached, he managed to Read More
VoIP Phones
VoIP phones are telephones which connect to VoIP networks instead of to the PSTN. VoIP phones with Ethernet connections VoIP phones with Wi-Fi / 802.11 connections VoIP phones with dialup modem connections Software VoIP phones VoIP Phones with Ethernet connections A VoIP phone with an Ethernet connection is the easiest type of VoIP telephone to use. Instead of a standard telephone RJ-11 connector to plug into the PSTN, these phones have RJ-45 connectors to plug into Ethernet networks. The Ethernet connection is used to connect these VoIP phones to the Read More
lsass.exe
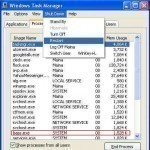
LSASS, or local security authority subsystem service, is a process that functions as part of the Microsoft Windows operating system. Essentially, LSASS is part of the process for maintaining and enforcing the security protocols on the operating system. To this end, LSASS performs several important functions to ensure that the system remains free from unauthorized access and is protected from a wide range of viruses and bugs. What does LSASS Specifically do? Perhaps the most common task that LSASS oversees is the access to a computer or server. LSASS recognizes Read More
Anchor Text

“Anchor text” is a term used in SEO science to describe the viewable term(s) in a hyperlink. Anchor text is used to create clean, easy-to-read links in a webpage without displaying raw information. While anchor text can be used as a word, phrase, or URL, the URL is generally omitted in a hyperlink that is using anchor text. Anchor text is most often used for SEO, or Search Engine Optimization, because search engines rate webpages higher in search results based on their relevant anchor text links. However, anchor text is Read More
Insertion of an Element in a Heap
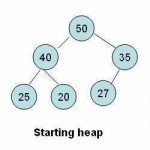
An element is initially inserted as the last child of the heap. On insertion, the heap remains a complete binary tree, but the order property may be violated. We have to perform a series of operations to move the element up from the last position until either it ends up in a position where the order property is satisfied or we hit the root node. In this tutorial, we refer to this process as the reheapify upward operation. Algorithm ReheapifyUpward(heap,start) Here heap is a linear array and start is the Read More
Touch Screen Monitors
A touch screen is basically a display screen which can identify the occurrence and position of a touch within its own area. This usually refers to a touch or tap to the display of the gadget by a finger or hand. Touch screens can also identify added inactive objects, such as a stylus. Touch screens work by recognizing the pressure of a finger or stylus and then responding accordingly. For a touch screen to work, it needs a few basic parts. These parts, when combined together, allow the touch screen to Read More
How to Find Broken Links
Broken links annoy the visitors to your web site, which lowers you percentage of return visitors. In addition, broken links on your web site may negatively affect your search engine rankings. Finding broken links on your web site can be accomplished by either a downloadable program such as Xenu Link Sleuth, or by using a web-based application such as the W3C Link Checker. Xenu Link Sleuth Xenu's Link Sleuth (TM) checks Web sites for broken links. Link verification is done on "normal" links, images, frames, plug-ins, backgrounds, local image maps, Read More
Pentium
The Pentium family of processors is the current generation of CPU's for personal computers from Intel. Pentium processors trace their heritage all the way back to the original Intel 8088 CPU used in the original IBM-PC in 1981. Intel renamed the 80586 processor Pentium because of the difficulties of trademarking numbers. This was a move by Intel to create confusion in the marketplace which would reduce commodotization in the CPU market and allow them to retain higher profit margins in the face of low-cost competitors like AMD. Intel retained the Read More
Easy PC Troubleshooter Pro

Easy PC Troubleshooter Pro is an application designed for the Android smartphone that allows users to solve a wide variety of computer related problems from their Android. Easy PC Troubleshooter Pro is ideal for users who have a computer that is running Windows 7, but may be used for any operating system. Easy PC Troubleshooter Pro is available from the Android Market for $0.99 and can be installed either directly or manually, depending on the user’s preference. How to Use Easy PC Troubleshooter Pro Programs that are designed to assist Read More
Depth First Search Algorithm
A DFS algorithm, as the name implies, is used to search deeper in the graph, whenever possible. The edges are explored, out of the most recently discovered vertex v that still has unexplored edges leaving it. When all of v's edges have been explored, the search backtracks to explore edges leaving the vertex from which v was discovered. This process continues until we have discovered all the vertices that are reachable from the source vertex. DFS uses stack structure to maintain the order in which the vertices are to be Read More


Share on: