How to Audit Windows NT/2000/XP Passwords
Microsoft Windows NT/2000/XP passwords are encrypted as 32-bit one-way hashes using the MD4 messages digest algorithm. This is similar to the way that Unix stores passwords, although the hashing algorithm is different.
For compatibility with legacy Microsoft LAN Manager software, Windows NT/2000/XP also stores the passwords redundantly as a 56-bit DES (Data Encryption Standard) hash. This 56-bit hash is created by splitting the password into two 7-character uppercase strings, and then converting each to a 56-bit DES key which both then encrypt the string “KGS!@#$%” and concatenating the results. This hash is usually referred to as the NTLM hash. This algorithm is poorly designed and impacts Windows network security in a significantly negative manner.
Windows NT/2000/XP passwords are vulnerable to a dictionary attack. This is much the same as attacking Unix passwords using a wordlist.
In addition, NTLM passwords are vulnerable to a brute force attack. This means that every password on the system can be retrieved.
Windows NT/2000/XP Password Auditing Programs
There is no “password file” under Microsoft Windows NT/2000/XP. Microsoft Windows NT/2000/XP stores encrypted password hashes in the Windows Registry.
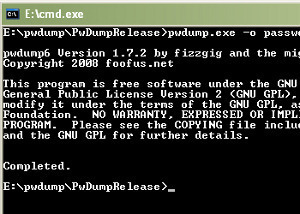
If you can access the Registry you can use PWDump by Jeremy Allison to view the password data.
PWDump output consists of seven colon delimited fields:
Username User number Encrypted password LAN Man Password Hash Windows NT Password Hash Full Name and Description Home directory
Sample passwd entry: will:1000:30FA7B24C6108C5A8B4BCCA42D5816FF: B3823C82B43238D31BAF98FA4035255F:Will Spencer, FAQ Author::
Broken down, this password entry shows:
| Username | will |
| User number | 1000 |
| Encrypted password | 5fg63fhD3d5gh |
| LAN Man Password Hash | 30FA7B24C6108C5A8B4BCCA42D5816FF |
| Windows NT Password Hash | B3823C82B43238D31BAF98FA4035255F |
| Full Name and Description | Will Spencer, FAQ Author |
| Home directory |
RDISK stores a compressed backup copy of the password hashes in %SystemRoot%repairsam._. If you can access this file, you may be able to restore it to another system and access the password information contained within it.
OpenWall’s John the Ripper with Olle Segerdahl’s NTLM patch: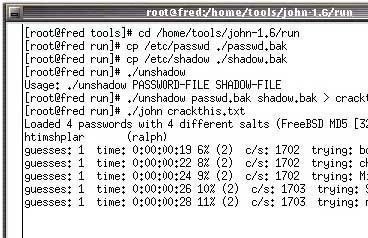
John the Ripper is a fast password auditor, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP LM hashes, plus several more with contributed patches.
Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kinds of passwords by sniffing the network, auditing encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.


Comments - No Responses to “How to Audit Windows NT/2000/XP Passwords”
Sorry but comments are closed at this time.