When software and hardware goes through development and testing, the time comes for it to be released throughout the IT infrastructure or to other clients. This falls on the lap of the ITIL Release Management team. This team of individuals ensures that the licensure, tests and version-verified software and hardware is all up to date upon release. This is to ensure that it functions properly when it is placed into the current infrastructure. During the development and implementation of new hardware is also a responsibility of the release management–specifically, the Read More
The Richter Scale
When earthquake generate seismic waves that travel through the Earth’s crust, they can be recorded on seismographs. When a seismograph records these waves, a trace that shows the amplitude of the wave measurements is generated and converted to the Richter Scale measurement. Depending on the sensitivity of the device, measurements can be made for earthquakes that occur a significant distance away from the measuring device. The Richter scale does not measure the damage that an earthquake causes, just the strength of it. This is because it cannot take into account Read More
What is a Laser Profilometer?

A profilometer is an instrument that measures a surface profile to determine its roughness. A surface’s vertical resolution is normally measured at the nanometer level, with lateral resolutions being measured to a less accurate degree. Over the past decade, profilometers have started using laser technology in order to improve the degree to which a surface can be measured without having to physically touch the profile being measured. The most recent laser profilometers have been able to map surfaces in 3D, thereby displaying form and texture over a large area. How Read More
IP Address Conflict
An IP (or Internet Protocol) address conflict occurs when two different systems on the same subnet are assigned or otherwise have their network interface configured to use the same IP address. It is possible to have two systems on different subnets configured with the same IP address, but not have a conflict occur due to routing limitations or because of the effects of NAT or Network Address Translation. Systems with the same IP Address on the same subnet need not have the same netmask or broadcast address for the conflict Read More
Understanding and Designing a Public Key Infrastructure
An Introduction to the Public Key Infrastructure (PKI) It has grown more important to ensure the confidentiality and integrity for data communication where an organization's network contains intranets, extranets, and Internet Web sites. Because of the connectivity of networks today, an organization's network is exposed to unauthorized users who could possibly attempt to access and manipulate mission critical data or the confidential data of its clients. The need to authenticate the identities of users, computers and even other organizations, has led to the development of the public key infrastructure (PKI). Read More
How to Transfer a PDF to a Kindle

A Kindle is a portable electronic device that Amazon provides, which allows users to read and access e-books when away from a computer. Kindles provide readers with a means of storing and reading thousands of books anywhere they go by organizing them as AZW files that can be displayed on the Kindle screen and accessed via keys on the front of the Kindle. What is AZW? The AZW file format is the Amazon Kindle’s official format and is used to allow the Kindle to read, store, and access e-books. The Read More
Qubit
A quantum bit, otherwise known as a qubit, is one of the units used when dealing with quantum information. Another way to look at a qubit is that it is a state vector which is an object of math that can describe different quantum systems. In the case of the qubit, that quantum system is a two-level quantum-mechanical system. One of the biggest discussions when dealing with the qubit is its comparison to the traditional or classical bit when dealing with computer information. Bit vs. Qubit A bit is one Read More
IS-54 and IS-136: TDMA
IS-54 and IS-136 are standards for TDMA American Digital Cellular. Mobile Frequency Range Rx: 869-894; Tx: 824-849 Multiple Access Method TDMA/FDM Duplex Method FDD Number of Channels 832 (3 users per channel) Channel Spacing 30Khz Modulation DQPSK Channel Bit Rate 48.6Kb IS-54 and IS-136: TDMA Security IS-54 and IS-136 use the CAVE (Cellular Authentication, Voice Privacy and Encryption) algorithm for authentication and the CMEA (Cellular Message Encryption Algorithm) for encryption. CAVE and CMEA are documented in Common Cryptographic Algorithms and Interface Specification for Common Cryptographic Algorithms. David Wagner, Bruce Schneier Read More
MD5 (Message Digest 5)
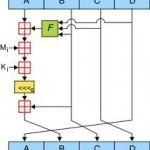
MD5 is a message digest algorithm. MD5 takes a variable length input and produces a 128-bit message digest. MD5 was designed by Ron Rivest in 1991. MD5 is officially defined in RFC 1321 – The MD5 Message-Digest Algorithm. MD5 Usage MD5 is used in many applications, including GPG, Kerberos, TLS / SSL, Cisco type 5 enable passwords, and RADIUS. Software Implementations of MD5 Ready-to-use MD5 implementations are available in C, C++, JavaScript, PERL, ActiveX, and Delphi. The Difficulty of a Brute Force Attack Against MD5 The difficulty of creating two Read More
How Bug Detectors Work

A bug detector is a device that is able to locate and/or disable electronic spy equipment such as microphones, cameras, and GPS tracking devices. Law enforcement agencies, military counter-intelligence agencies, criminals, and everyday individuals who are suspicious of being overheard often use bug detectors. Bug detectors are usually small, portable, and have multiple display functions to alert the user to a “bug.” How Bug Detectors Work A bug detector is essentially a radio receiver that is able to pick up electromagnetic signals that are broadcasted from an electronic device or Read More


Share on: