Tor is a program that is able to hide the user’s online activities from third parties and prevent websites from seeing where the user is browsing from by rerouting the user’s sent and recieved data through the Tor Network. The Tor Network is made up of hundreds of volunteers from around the world that specifically setup their Tor client as a relay station for other users. Tor does have its downsides, however, as it blocks a number of browser plugins and it must be specifically configured for each application that Read More
How to Delete Recent Searches
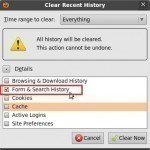
Deleting recent searches–be they from Bing, Google or Yahoo–is an easy thing to do. While the steps vary a little from Internet Explorer to FireFox, for the most part, they take the same amount of time and can be found in the same place. Deleting Recent Searches in Internet Explorer Click on the tools button. Based on which version of Internet Explorer you’re using, you can find the tools button either at the top or to the right. If it is to the right, you’ll find it right before you Read More
How to Set up a VPN
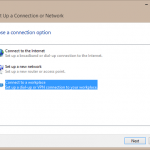
A Virtual Private Network (VPN) is typically used by companies, schools, and other organizations when they want to allow remote access to their servers, printers, and other network devices without compromising security. A VPN therefore extends a private network across the internet, but protects this connection by encrypting it, thereby creating what many refer to as a tunnel through the public internet. VPNs have other uses though, such as securing your internet connection to protect your privacy and allow you to bypass censorship. Ideally, everyone should consider using a VPN, Read More
How to Hide an IP
Hiding an IP online is necessary for a variety of reasons. Various websites, video games, and miscellaneous connections to the Internet share information about the network’s location and host. The simplest way to prevent sharing this information, while still being able to connect to the Internet is by hiding the individual’s and his/her Internet enabled device’s IP address. To do this, the user has to use a proxy server to hide the original IP. The Benefits of Hiding an IP Hiding an IP usually provides the following benefits: Anonymous Surfing Read More
How to Remove all Personal Files from Windows
Over the last decade, millions of people have kept more and more personal information on their computers. From credit card numbers to sensitive emails and word documents, a vast amount of personal files are on almost any home computer. While keeping personal and sensitive information on a home computer is relatively safe, if you plan on throwing out your computer, selling it, or even selling just the hard drive, you may be allowing others easy access to all your personal files. Here are some tips on how to remove these Read More
Why Everyone Should Use a VPN

VPN, or a Virtual Private Network, connects computers and other devices using an encrypted connection. This means that all data travelling through such a network is unreadable to anyone who might intercept the data stream, making it as private as it would be if all of the connected devices resided within the walls of a private property (like your home). In other words if you connect your computer to a VPN, and route all of your online activity through it, this activity can no longer be tracked by your internet Read More
How Do I Clear Previous Google Searches?
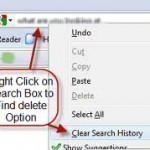
Clearing previous Google searches is a straight forward process that can take about one minute to accomplish. It should be noted that unless you’re using the Google toolbar, erasing only the history of Google is impossible. However, since people typically only use one search engine predominately, erasing the search history will only affect Google. Erasing Search History in Internet Explorer To erase the history, look for the tools tab. Depending on what version of IE being used, one can determine where the tools tab is located. Click the tools tab Read More
How to Erase History on a Computer
Erasing the history on a computer is very important for personal safety. There are two main types of history that computer users may want to remove from a system: the Windows and Web Browser history. There are several different locations where computer usage information is stored in Windows. Modern Windows operating systems are preconfigured to track everything from recently opened documents, search items, save history, and run history. The process of removing this personal information is relatively simple if these steps are followed: Recently Opened Documents in Start Menu – Read More
Technologies That Can Help Protect Your Privacy

In a previous article on privacy we’ve established what it is, how does digitally networking our world affect it, and in a nutshell, why should we care. We established that the best way to ensure your privacy is through technological means, and in this article I offer an overview of what such technologies are. What is common to all of them is that they let you control access to information about yourself, whether it is your location, sites you visit, conversations you have online, things you post about yourself, and Read More
Anonymous Surfing

Anonymous browsing is simply browsing the World Wide Web with most of one’s identity hidden. This is primarily done through what is known as an anonymous browser based proxy. These websites hide information such as the computer’s location and IP address when users use them to browse the web. For example, when the user tries to access something on a certain part of the web, the proxy will talk to that file as the user’s ambassador, maintaining the user’s privacy. The practice of anonymous browsing can also maintain the user’s Read More


Share on: