Root Certificate
A Root Certificate is a self-signed certificate or an unsigned public key certificate which forms an important part of the PKI (public key infrastructure). The most common commercial type of root certificates is based on the ISO X.509 standard. Such a certificate (a X.509 certificate) usually carries the digital signature of a certification authority (CA), which is the authorized body for validating the embedded data.
In most enterprise-scale public key infrastructure systems, certificate chains prove or verify the identity of a party. When the certificate is issued by a certification authority, it becomes mandatory that the legitimacy of that certificate authority be certified. This is usually done by a higher certification authority in a veritable chain of command model. However, this chain will end somewhere and that ending stop is known as a root certificate. It is so called because it is the root of the certificate tree or the monarch of the certificate domain.
The Certification Authority is more like the branches of the certificate tree (or the ambassadors of the certificate domain) because they have the capability of extending multiple certificates. 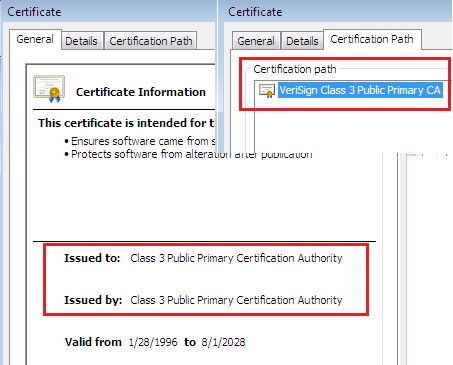
The advantage or disadvantage of root certificates is that they are implicitly trusted. For example, root certificates are included in software applications such as the web browsers – Internet Explorer, Mozilla, Netscape, and Opera – where they play a major role in securing TTL/SSL connections. Such a design, by implication, would mean that the user has to trust the browser’s publisher to include a genuine root certificate, and in the process, the certification authority it trusts. They must also trust anyone to whom that particular certification authority has given the ability to issue a certificate to honestly authenticate the owners of all their certificates. The interesting and intriguing point to be made is this transitive trust is generally taken for granted. There is no practical way to ensure that the entire certification chain is error free. Most web users have no choice but to live with this potential hazard as long as most of the certification authorities prefer to follow the X.509 certification chain model.


Comments - One Response to “Root Certificate”
Sorry but comments are closed at this time.