Linksys is the home networking division of Cisco, Incorporated and has significant penetration in the U.S. home networking market. A common question that arises for consumers who are new to home or small business networking is determining how to find a Linksys router IP address on a new or legacy network. When shipped from the factory, a Linksys broadband router’s IP address is 192.168.1.1 which is set at the factory. If the end-user needs to change the address due to conflicts with other networking devices on the local or home Read More
traceroute
traceroute is a command which is used to trace the route of a packet through a TCP/IP network. traceroute is a Unix command. Under Microsoft Windows, the traceroute command has been renamed `tracert`. Unix `traceroute` and Microsoft Windows `tracert` are designed to accomplish the same task, but differ in the way they display output, in the way they send test packets, and in the number of command line options they provide. Sample `tracert` output This is the result of tracing the network route to www.mit.edu: C:>tracert www.mit.edu Tracing route to Read More
MPLS (Multi Protocol Label Switching)
MPLS stands for Multi Protocol Label Switching. The MPLS is often referred to as the layer in between the Data Link and Network layers because of where it operates. The MPLS serves as a method to forward packets of data easily by using labels. What are the Data Link and Network layers? In the seven-layer OSI model, a model used to explain how a computer operates and communicates within itself. The Data Link and Network Layers are parts of this model, and correspond to the second and third layers respectively. Read More
Routing Table
A routing table is an electronic document that stores the routes to the various nodes in a computer network. The nodes may be any kind of electronic device connected to the network. The Routing Table is usually stored in a router or networked computer in the form of a database or file. When data needs to be sent from one node to another on the network, the routing table is referred to in order to find the best possible route for the transfer of information. Hop-by-hop Routing is a common Read More
MPLS VPN
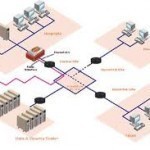
An MPLS VPN (Multi-Protocol Label Switching Virtual Private Network) is a virtual private network that uses MPLS to forward data packets from one device to another by tunneling through the Internet. MPLS VPNs transfer any data packet type to any device within the network and can be used for many applications including communication, data transfer, and information access on the network’s client and server side. How MPLS VPNs Work MPLS VPNs create a tunnel through the Internet in which two or more devices can exchange information. In order to do Read More
What is NetBEUI?
NetBEUI (NetBIOS Extended User Interface) is an extended version of NetBIOS, the primary software that allows individual computers to communicate within a given local area network. While NetBIOS itself is most often used to transfer pictures, documents, videos, or other files from one computer to another, NetBEUI is responsible for arranging the actual information in a data transmission. As a result, NetBIOS cannot transfer files or share access rights between two computers without the NetBEUI extension. How NetBEUI Works NetBEUI is neither its own stand-alone program nor its own protocol. Read More
Frame vs Packet
A packet and a frame are both packages of data moving through a network. A packet exists at Layer 3 of the OSI Model, whereas a frame exists at Layer 2 of the OSI Model. Layer 2 is the Data Link Layer. The best known Data Link Layer protocol is Ethernet. Layer 3 is the Network Layer. The best know Network Layer protocol is IP (Internet Protocol). To move through a network, a packet is encapsulated into one or more frames, depending upon the MTU size.
What is an L2TP?
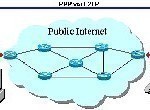
L2TP (Layer Two Tunneling Protocol) defines an extension to PPTP (Point-to-Point Tunneling Protocol) that an ISP (Internet Service Provider) uses to allow a VPN (Virtual Private Network) to operate. L2TP combines L2F from Cisco Systems’ optimum features and PPTP from Microsoft into a single protocol. L2TP’s two primary components are the LNS (L2TP Network Server) that terminates and authenticates the PPP stream and the LAC (L2TP Access Concentrator) that physically terminates a call. How does L2TP Work? The L2TP initiates a tunnel between an LAC and an LNS on the Read More
Network Routers
A network router is a network device with interfaces in multiple networks whose task is to copy packets from one network to another. Routers operate at Layer 3 of the OSI Model, the Network Layer. This is in contrast to switches, which operate at Layer 2 of the OSI Model, the Data-Link Layer. A network router will typically utilize one or more routing protocols, such as RIP, OSPF, or BGP. Routers also accept routes which are configured manually by a network administrator. Those routes are called static routes. The router Read More
IP (Internet Protocol)
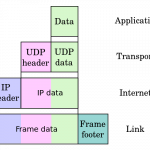
The primary network communications protocol used on networks today is the IP (Internet Protocol). IP relays or transfers network packets, also known as datagrams, to destinations on local networks or across the public Internet. It defines the structures which encapsulate information as well as the legal addressing methods used to identify the source and destination network hosts or computing devices. When first introduced in 1974, IP was the datagram service included with the TCP (Transmission Control Program) protocol providing a connectionless service coupled with the connection-based TCP protocol. As a Read More


Share on: