Ethernet is the most common LAN (Local Area Network) technology in use today. Xerox developed Ethernet in the 1970s, and became popular after Digital Equipment Corporation and Intel joined Xerox in developing the Ethernet standard in 1980. Ethernet was officially accepted as IEEE standard 802.3 in 1985. The term “Ethernet” is now used to refer to all derivatives of the original Xerox “Ethernet”. Ethernet Speeds The original Xerox Ethernet operated at 3Mbps. Ethernet became popular as a 10Mbps standard over coaxial or twisted pair cabling. Fast Ethernet improved speeds to Read More
ISDN Modem
ISDN – otherwise known as integrated services digital network – is a digital phone connection that can transmit data, voice and video over a normal telephone line. It was meant to be a method of transmitting information much faster than a typical analog phone; however, the phone industry was able to survive the arrival of the ISDN and these days, is stronger than ever. Therefore, ISDN has diminished in use; however, those that do provide it as a service target high-traffic businesses that need the ability of sending information and Read More
ISDN BRI
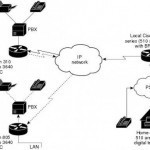
ISDN BRI (Basic Rate Interface) is a standard Integrated Services Digital Network (ISDN) service meant for residential and small scale business Internet connections. There is another type of ISDN configuration called the Primary Rate Interface (PRI) that is designed to provide higher bandwidth. The BRI configuration defined in the physical layer standard I.430 produced by the ITU. Both the BRI and PRI are designed similarly. That is, both make use of the B and D channels for data communication, but in different combinations. B Channel or the Bearer Channel is Read More
VLAN (Virtual Local Area Network)
VLAN (Virtual Local Area Network) is a logical local area network (or LAN) that extends beyond a single traditional LAN to a group of LAN segments, given specific configurations. Since a VLAN is a logical entity, its creation and configuration is done completely in software. How is a VLAN Identified? Since a VLAN is a software concept, identifiers and configurations for a VLAN must be properly prepared for it to function as expected. Frame coloring is the process used to ensure that VLAN members or groups are properly identified and Read More
ADSL Router
An ADSL router is also known as a DSL modem. The router connects the computer to the DSL phone line so the ADSL service can be used. Some countries also use the term NTBBA (Network Termination BroadBand Access). There are some ADSL routers that are also capable of sharing a single Internet connection with a group of computers on a network. This system is also known as the residential gateway. The ATU-R Every ADSL router has a functional block called ADSL Terminal Unit-Remote (ATU-R (transceiver). The ATU-R is responsible for Read More
VDSL (Very High Bit-Rate Digital Subscriber Line)
Broadband has revolutionized the way we view and use the internet. The two main types of broadband technology that have pervaded the market are Asymmetric Digital Subscriber Line (ADSL) and cable modems. Both these technologies are a huge leap from the days of the 56 Kbps dial-up connections, with maximum speeds ranging between 8 to 10 Mbps. This makes one wonder, what’s next? Another form of DSL, known as VDSL or Very High Bit-Rate Digital Subscriber Line, is widely regarded as the next step in Internet connectivity. This technology is Read More
Ethernet Cable Pinout
Ethernet cable connects a network interface card (NIC) with a hub or Ethernet switch. Ethernet cables can be purchased from a computer store. They come in two categories, flat and braided. The flat or solid cable is used when there is a need for a longer cable run. However, it is not flexible. Thus, its position is fixed. The braided cable is easier to use and is more flexible. However, it is useful only in places where a shorter cable run is needed. In the Ethernet cable pinout there are Read More
How to Clear the ARP Cache
ARP (Address Resolution Protocol) Cache is a technique used to store “mappings” of OSI Model Network Layer addresses (IP addresses) to corresponding OSI Model Data Link addresses (MAC addresses). Due to a variety of possible circumstances, ARP cache can become damaged requiring the end user or administrator to determine how to clear the ARP cache for the respective computer system or device. Symptoms that the ARP cache requires clearing include the computer’s operating system failing to function properly, numerous websites failing to load, and interruptions in network or Internet connectivity. Read More
Broadband over Power Lines
Broadband over Power Lines, or BPL, refers to the transmission (sending and receiving) of digital data through existing power cables and electricity distribution infrastructures. This can be viewed as a mere variation on using television cables; instead of using television cables, though, power transmission lines are going to be used. The Broadband over Power Lines Transmission Architecture The key to broadband over power lines (Broadband over Power Lines) technology lies in a long established scientific fact: radio frequency (RF) energy can be bundled on the same line that carries electrical Read More
VLAN Hopping
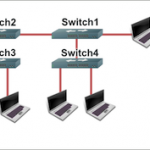
VLAN Hopping is one of the primary VLAN based attacks used by hackers to infiltrate network security. VLAN hopping is used to attack a network by sending packets to a port which is generally not accessible. VLAN hopping attacks are mainly conducted in the Dynamic Trunking Protocol and, in some cases; the attacks are targeted to the trunking encapsulation protocol (802.1q or ISL). The Dynamic Trunking Protocol is utilized for negotiating trunking on links between devices and the type of trunking encapsulation to be used. Types of VLAN Hopping Switch Read More


Share on: