What is Windows Security Alerts Windows Security Alerts is a security feature of the Windows operating system that warns users when there are security-related issues. Windows Security Alerts is directly connected to the Windows Security Center and may present information concerning the user's firewall, network, or computer itself. Windows Security Alerts is especially helpful when the computer is infected by a virus or other malicious software as it warns the user that his/her computer might be infected. How To Disable Windows Security Alerts As Windows Security Alerts can be irritating Read More
How to Turn off User Account Control
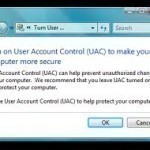
Microsoft designed the Windows User Account Control and deployed it on the Windows Operating System (OS) in order to prevent unauthorized modifications to critical settings or programs on a computer running the Windows OS. Microsoft deployed User Account Control since Windows XP, and has continued to update the application in newer versions of Windows (such as Vista and Windows 7). Users often want to disable User Account Control in order to prevent the OS from displaying warning boxes. How to Turn Off User Account Control – Windows XP Step 1 Read More
Designing Network Infrastructure Security
Network Infrastructure Security Overview Network infrastructure refers to the grouping of physical hardware and logical components which are needed to provide a number of features for the network, such as connectivity, routing and switching capabilities, network security, and access control. The physical infrastructure of the network refers to the physical design of the network together with the hardware components. The logical infrastructure of the network consists of all the software components required to enable connectivity between devices, and to provide network security. The network's logical infrastructure consists of software products Read More
How to Limit Internet Access in Windows XP User Accounts

User accounts allow Microsoft Windows to differentiate between computer users in order to determine the rights they should have. Each user account is assigned its own location on the hard disk for file storage. There is a collection of settings pertaining to each account that is stored in the computer’s Registry. Methods for Limiting a Windows XP User Account’s Internet Use Windows SteadyState Windows SteadyState is a free, discontinued Microsoft product that can still be downloaded from many online sources. It allows users to make changes to how their computer Read More
How to Run as Administrator
Running as administrator simply means that you are in logged into your Microsoft Windows computer as the administrator role which has the ability to install programs and do anything else. The administrator is the account that can make all changes to the computer. However, security experts warn against running in an administrator account because if a virus gets into the computer, it typically functions off of a permission based system. In other words, because the administrator can do anything on a computer, a virus can execute anything if it comes Read More
How Internet Authentication Service (IAS) works
Internet Authentication Service (IAS) is Microsoft's implementation of a RADIUS (Remote Authentication Dial-in User Service) server and proxy. As a RADIUS server, IAS performs centralized connection authentication, authorization, and accounting for many types of network access, including wireless and VPN (Virtual Private Network) connections. As a RADIUS proxy, IAS forwards authentication and accounting messages to other RADIUS servers. The Authentication and Authorization Processes When a user tries to connect to a dial-up connection server or a Network Access Server (NAS)/Virtual Private Network (VPN) Server the following authentication requests are performed: Read More
Identifying Security Issues Common to All Server Roles
Physical Security Issues Server security is basically one of the initial security requirements when you install any server operating system. Servers have to be physically secure from physical threats such as physical unauthorized access. Physical security prevents an individual from physically accessing your server, and performing malicious actions. A few guidelines and recommendations for implementing physical server security are detailed below: All servers should be secured in a locked server room. Only those individuals that need access should be permitted to access the server room using a key or security Read More
Securing Mail Servers
Mail Server Role Security Issues Mail servers store e-mail data, process client requests, and receive incoming e-mail from the Internet. The Post Office Protocol 3 (POP3) protocol provides clients with mailboxes and enables mail to be retrieved from the mail server. The e-mail accounts of users are POP3 accounts, and are stored on the configured mail server. POP3 makes is possible for clients to use Microsoft Outlook, or some other e-mail client to retrieve e-mail from the mail server. The Simple Mail Transfer Protocol (SMTP) protocol is utilized to transfer Read More
Planning Server Security
Server Roles Review The physical hardware and logical components of the network are necessary to provide a number of features for the network, such as connectivity, routing and switching capabilities, network security, and access control. The network infrastructure has to exist before the servers needed to support services and applications which are required by your users can be deployed into your networking environment. While Windows Server 2003 provides a number of features and tools when you install it on a computer, you have to implement additional features and functionality on Read More
Configuration of Windows Login Interface
The level of access that one has to his/her Windows machine depends on whether the Windows Login interface is enabled or disabled. When the logon screen is enabled, the user is prompted to select an account username and put in a password for the account selected. This allows users to access a single computer via many accounts when it has been preconfigured for this purpose. Individuals who are the sole users of their computer prefer to disable the Windows logon screen. They may also use a single account and therefore Read More


Share on: