Domain and forest functional levels provide a means of enabling additional domain and forest-wide Active Directory features, remove outdated backward compatibility in an environment, and improve Active Directory performance and security. In Windows 2000, the terminology for domain functional levels was domain modes. Forests in Windows 2000 have one mode and domains can have the domain mode set as either mixed mode or native mode. With Windows Server 2003 Active Directory came the introduction of the Windows Server 2003 interim functional level and Windows Server 2003 functional level for both Read More
Active Directory Objects
The Active Directory data store, also referred to as directory, contains data on users, groups, computers, and on which resources these users, groups, and computers can access. It holds all Active Directory information. Each domain controller within a domain holds a readable/writable replica of the Active Directory data store that consists of information pertaining to the particular domain to which it belongs. Users and computers can continue to access the Active Directory data store when one domain controller in a domain is offline because they can use any other domain Read More
Active Directory Replication
The initial Windows NT versions were designed as single master network environments. The primary domain controller (PDC) was responsible for managing the domain database’s master copy. The PDC was therefore responsible for replicating any changes to the backup domain controllers (BDCs). In these environments, any changes had to be performed on the PDC, which then replicated these database changes to the BDCs. What this meant was that in cases where the PDC was unavailable, no changes were made to the domain database. From this simple discussion, it is clear that Read More
Implementing Folder Redirection with Group Policy
An Overview on Folder Redirection Folder Redirection is a Group Policy feature that enables users to redirect the system folders containing the profile of a user on the network, through the use of the Folder Redirection node in the Group Policy Object Editor console. This basically makes folder redirection a user configuration option. Through the use of the Folder Redirection feature, users can configure that the system folders’ contents on the user remains the same, irrespective of the particular computer used to log onto the system. The system folders that Read More
Group Policy
Group Policy gives users administrative control over people and computers in the user’s network. By using Group Policy, users can define the state of someone’s work environment once, then rely on Windows Server 2003 to continually force the Group Policy settings applied across an entire organization or to specific groups of people and computers. Group Policy Advantages Users can assign group policy in domains, sites, and organizational units. Group policy settings reflect all persons and computers in domain, site, and organizational unit. No one in network has rights to change Read More
Active Directory Security
Active Directory security is determined by the following components: * Security groups: A security group is a made up of a set of users, and is created to assign permissions to access resources, and to assign user rights to group members. Permissions control access to resources, while user rights define what actions users can perform. Security groups are considered security principal accounts because they can contain user accounts. It is the security principal accounts that are used in authentication and access control. The security settings of a security principal account Read More
Logical Structure of an Active Directory
Active Directory fulfills all the needs of an organization by designing a directory structure. It provides flexibility in designing the business structure according to current and future needs for an organization, so it should be examined prior to installing active directory. In Active Directory, resources are organized in a logical structure, and this grouping of resources logically enables a resource to be found by its name rather than by its physical location. Benefits of AD Logical Structure Logical Structure provides more network security by means of providing access to resources Read More
Understanding Active Directory
The Limitations of the Windows NT Domain Model and Network Security With Windows NT, domains were utilized to manage users, and to manage and secure network resources. A domain is the logical grouping of servers and network resources under a single domain name. In Windows NT, a domain could be considered as a central database containing security information which was then basically used to manage users and network resources. The Windows NT computers operated as domain controllers, with each domain essentially having one Primary Domain Controller (PDC) and one or Read More
Understanding Organizational Units
An organizational unit (OU) is a container that logically organizes and groups Active Directory objects within domains. OUs are not part of the DNS namespace. They organize Active Directory objects into logical administrative groups. OUs therefore serve as containers in which users can create and manage Active Directory objects. OUs are considered the smallest unit to which an Administrator can assign permissions to resources within Active Directory. An OU enables users to apply security policies, deploy applications, delegate administrative control for Active Directory objects, and run scripts. An important thing Read More
Active Directory Authentication Types
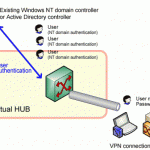
The two types of authentication are Mutual Authentication and NTLM. Mutual Authentication requires both the server and the client to identify them. NTLM only requires the client to be validated by the server. Two types of authentication are Mutual Authentication and NTLM Authentication. Mutual Authentication Mutual Authentication is a security feature in which a client process must prove its identity to a server, and the server must prove its identity to the client, before any application traffic is sent over the client-to-server connection. Identity can be proved through a trusted Read More


Share on: