The application layer of a software is a protocol that is used for communication between a software and the network layers that it uses. The application layer allows a computer’s network to interpret requests made by the program and allows the program to interpret data from the network. Likewise, the application layer ensures that both parties are available and can communicate with another, authenticates messages from both parties, and ensures that both parties agree about privacy, data integrity, and error recovery. How An Application Layer Works The application layer Read More
Degaussing
Degaussing is a process of reducing the magnetism of a material by applying an opposite magnetic field. The name is derived from a unit of magnetic flux, the gauss. There are many different uses for degaussing. Cathode Ray Tubes Most televisions and computer monitors that use cathode ray tubes have a degaussing function. The electron beams cause a magnetic field to build up on the shadow mask, and this changes the path of the beams causing the picture to warp. An insulated bundle containing many turns of copper wire is Read More
Quantum Dots
A quantum dot is a semiconductor that exhibits tremendous capability despite the fact that they are so tiny: 2-10 nanometers. Because materials behave much differently when they are at this size, researchers hope that they will be able to make tremendous steps in many different applications of science and technology. Because of the size of them, the quantum dots provide the researcher with the ability to tune the dots to levels that have never been reached before. To describe it in a much more straight forward manner, a quantum dot Read More
Monitoring, Tuning and Troubleshooting Proxy Server
Optimizing Proxy Server Performance In order to optimize server performance for whatsoever reason, you need to start by monitoring the server. In most cases, before server monitoring commences, it is common practice to establish baseline performance metrics for the specific server. Baseline performance metrics are established by measuring the performance of a particular server under various conditions, at different times of the day, week, and month, and when the hardware and software configuration changes. Based on the baseline metrics which you define for the server, you would need to optimize Read More
What Are Bucky Balls Used For?
A bucky ball is a fullerene molecule which is any molecule that is made up entirely of carbon. Specifically, a bucky ball is a spherical fullerene while the cylindrical fullerene is called a carbon nanotube. They were discovered in 1985 and are referred to, chemically, as C60. When they were discovered, it expanded the number of carbon allotropes–the way the atoms are aligned–which had, before this, been diamond, graphite and soot/charcoal. Now fullerene molecules adds another allotrope to the mix. Because scientists are still working hard on determining what bucky Read More
How to Change the Font on an iPod

iPod is a portable media player created and sold by Apple Inc. It is by far the most popular and largest selling portable media player till date. iPod stores media files on a built-in hard drive. iPod has a number of add-on features such as address book, alarm clock, text reader, games, photo slideshow viewer and so on. Video content can also be viewed on an iPod. It has a maximum storage capacity of 160 GB. The iPod range presently includes the following: iPod Classic iPod Touch iPod Read More
Impact Printers

An impact printer is one that depends on a forceful impact to transfer ink to a material such as a t-shirt, sign, or sheet of paper. Impact printers differ from digital, inkjet, and inkless printers as it actually collides with the material itself. Typewriters, industrial printers, and daisy wheel printers are all forms of impact printers. Impact printers have many uses although they have generally been considered obsolete since the introduction of more modern printing techniques. How Impact Printers Work In a typical impact printer, a mesh, cloth, or ridged Read More
DigiCipher II

DigiCipher II (DCII) is a Motorola proprietary digital video distribution system. DigiCipher II provides compression, encryption, and authorization. DigiCipher II compression is based upon MPEG-2. DigiCipher II is utilized for some TVRO transmissions. A Motorola 4DTV satellite receiver is required to decode DigiCipher II TVRO channels. DigiCipher II utilizes AC3 audio encoding.
XML Tutorials
XML Tutorials XML stands for eXtensible Markup Language and it’s designed to store and transport data. Like HTML, it is a markup language that’ designed to carry data, and not to display data. XML is not a replacement for HTML. Basically. it’s just created to structure, and transport information. Just sort of like an information that is wrapped in tags. Below are some of our XML tutorials to know more about it. XML Document Tutorial A tutorial that shows how to create XML Document In an XML file there can Read More
Wireless Mesh Network
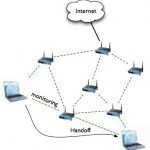
A wireless mesh network relies on radio signals to allow several devices within a coverage area to communicate with each other. Wireless mesh networks are often used in conjunction with other networks in order to give users reliability and stability. This is because wireless mesh networks communicate with each other through any device within the coverage area and automatically restore communication if one device stops working. Wireless mesh networks include everything that other networks do (router/gateway, clients, etc.) but do not necessarily need to connect to the Internet. How Wireless Read More


Share on: