Fixed Radio Scanners My recommendations for general purpose radios for scanning are the PC controlled models. PC controllers scanning radios give you many more options for playing and are a great bang for your scanning buck. The only downside is that you can't carry these radios around on your belt! Icom PCR-1000 WinRadio Mobile Radio Scanners To scan while walking around, I recommend either the Uniden BC250D Trunked Radio Scanner, which will enable you to listen to trunked radio, or the Yaesu VX-7R tranciever, which will allow you to both Read More
Where Are Visited Links Stored?
If you use Microsoft’s Internet Explorer, you probably have realized that for web pages you have already visited, these links are no longer blue, but purple. Every time you click on a blue link, when you return to that page within a short period of time (usually less than three weeks) the link will be purple to indicate that this link has been visited. While this indication can be helpful, many IE users wonder where these visited links are stored. Here is the answer: Visited Links are a feature of Read More
What is TrueCrypt?
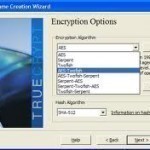
TrueCrypt is a free, open source disk encryption software that is available for the Windows XP, Windows Vista, Windows 7, Mac, Linux, and Unix operating systems. TrueCrypt provides users with real time encryption/decryption, parallelization and pipelining to read/write to partitions as fast as non-encrypted partitions, and plausible deniability through hidden volumes and hidden operating systems in order to hide the user’s data even if he/she is forced to reveal his/her password. How TrueCrypt Works TrueCrypt works by creating a virtual encrypted disk within a file and mounting it as Read More
Blue Screen of Death
If you have been working on computers or are just starting to use them, one of the most disturbing events that can occur is the BSOD or Blue Screen of Death. The BSOD is actually an error screen that is displayed by specific operating systems informing the user that a critical system error has occurred. The Blue Screen of Death can be found on many different types of operating systems, but is most notably infamous for occurring on Microsoft Windows Operating Systems. Common Causes of the Blue Screen of Death Read More
How to Edit Photos on Google Plus
Google Plus is Google’s new way of offering the latest social networking tools. In Google Plus, users add friends through a different interface that uses “circles” to sort friends by group, priority, and sharing status. Users can upload and create photo albums like Facebook on Google Plus. However, most users have no idea that they can actually edit their photos from Google Plus. Below are instructions on how to edit photos from Google Plus: 1. Log into your Google Plus account by visiting https://plus.google.com/. 2. Open the photos tab in your Google Read More
How to Update an Xbox 360

The Microsoft Corporation updates Xbox 360 software when new features or problem solutions for the console are available. Some of the common problems that game players experience that indicate the need to check for available updates include the dashboard themes not working or appearing on the console display, missing avatars, or the kinetic sensor not working. Since everyone does not use the xBox 360 in the same manner, Microsoft created four methods to update the software on the console: using xBox Live, installing from a game disc, copying to a Read More
Are there any Good Alternatives to eBay?

When most people want to buy or sell something over the Internet, they turn to eBay. It is one of the most popular auction sites used today. However, there are other sites that also offer such services. After all, it is always good to know whether or not you can find “it” elsewhere. Two alternatives are Yahoo Auctions and Bidville Auctions, two of the larger options available. Both have over a million listings, and this number seems to be increasing. There is, however, numerous others that may have smaller listings Read More
Declination
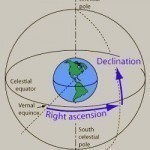
Declination is a coordinate system that uses Latitude that is then projected on large arbitrary radius measurements around the Earth that rotate on the same axis. Declination’s main purpose is to locate a specific object or point in the sky. It is measured in a value of degrees north and south of the celestial equator. These values are positive if north of the celestial equator, zeroed if equal to the celestial equator, and negative in the south. For example, the following values are true for declination positions from the celestial Read More
What Are the Benefits of PHP?
The programming language called PHP is quickly rising to be one of the most preferred web browser programming languages due to its user-friendliness, efficiency, and user control. PHP allows a user to describe specific functions within the code in order to drastically control the way a web browser displays and organizes information. A user is able to mix PHP and HTML within the same document to reach the desired effect. In this article, we will talk about how PHP works and why it is preferred by the people who use Read More
How to Lock a Keyboard

Many people install security features on their computer in order to prevent unauthorized users from accessing the computer when they are away. For example, login identification, file encryption, and even biometric identification are all sufficient methods of keeping intruders out of someone’s personal information. However, some users may wish to go even further by locking their keyboard in order to prevent unauthorized users from entering a password, children from playing with the keyboard, or pets from unknowingly typing when climbing on keys. There are several ways to lock a keyboard Read More


Share on: