What is Fingerprint Identification? Fingerprint identification is the process of using fingerprints to identify an individual. This is very effective because each person has completely unique fingerprints that do not change with age. Fingerprint identification is used for a variety of reasons: security, criminal investigations, and even ergonomics. Fingerprint identification often consists of a fingerprint reader or oil smear, with the former being used in electronic fingerprinting and the latter being used in manual fingerprint impressions. Other surfaces or materials may be used in fingerprint identification but are usually only Read More
S Band

S band is a frequency range from approximately 2 to 4 GHz. S band is used for Digital Audio Radio Satellite (DARS) satellite radio systems such as Sirius XM Satellite Radio. Sirius XM uses frequencies between 2,320.00 and 2,332.50 MHz, and also between 2,332.50 and 2,345.00 MHz. S band is also used by many weather, communications, and intelligence satellites. Most of these satellites transmit using CW, usually with sidebands. PSK with a sub-carrier is a less popular option. A portion of the S band from 2.4 to 2.4835 Ghz is Read More
Breadboard
A breadboard is a thin rectangular piece of insulating material used to hold electronic components when making circuit prototypes. They have many rows and columns of conductive points for inserting component terminals and jumper wires. The original breadboards were just wooden boards, presumably used to cut bread on, but the modern versions have plastic cases containing many spring-metal strips. Breadboards come in many sizes, from less than one hundred connection points to several thousand points. Some breadboards even come with larger components already connected, like displays and speakers. Breadboards are Read More
NetBEUI
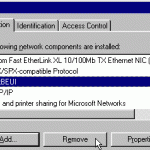
NetBEUI (NetBIOS Extended User Interface) is a program used for communication between applications installed on separate computers within the same LAN (Local Area Network). It is an upgraded version of NetBIOS and provides much more flexibility and functionality by rearranging the information in a data transmission. Like NetBIOS, NetBEUI is not a networking protocol and must be used in conjunction with IPE or TCP/IP in order to operate. How NetBEUI Works NetBEUI assigns a name to each application to be used within it. It then displays the name or IP Read More
Firefox for Mac

Firefox is an open source web browser that the Mozilla Foundation manages, which uses tabbed browsing, plug-ins, and a volunteer based support group to provide users with the most advanced web browsing features available. Since Firefox is an open source, it is constantly being updated to fit the needs of the current trends and market. Firefox is similar to many other web browsers, but allows anyone to create new features, plug-ins, and other scripts to change the way Firefox works, which other Firefox users can download and install. Firefox Read More
Dijkstra Algorithm
Dijkstra algorithm gets its name from the Dutch computer scientist Edsger Dijkstra who invented this algorithm in 1959. It is used to find the shortest path between two non-negative nodes in a graph. Dijkstra algorithm is widely used for the purpose of routing. For any giving node in a graph the algorithm finds the path which is the shortest from that node to all the corresponding nodes in the graph. As stated earlier also that this algorithm is used to find the shortest path between two distinct nodes on the Read More
Responding to Network Attacks and Security Incidents

Network Attacks Review A network attack occurs when an attacker or hacker uses certain methods or technologies to maliciously attempt to compromise the security of a network. Hackers attack corporate networks to use data for financial gain or for industrial espionage, to illegally use user accounts and privileges, to run code to damage and corrupt data, to steal data and software, to prevent legitimate authorized users from accessing network services, and for a number of other reasons. External attacks are performed by individuals who are external to the target network Read More
Biometrics
Biometrics, or bio-identification, is the practice of measuring physical characteristics of a person to verify their identity. The most common biometric systems measure fingerprints or hand prints. More advanced biometric systems measure the users voice, features of the users eyes, or the geometry of their entire face. Futuristic systems measure the users ears, their smell, or even their DNA itself. Biometrics are more secure than passwords, but they can also be fooled. For example, one hacker discovered that fingerprint readers could be fooled by copying a fingerprint using the goo Read More
How Does Lemon Juice Conduct Electricity?
Lemon juice has a natural pH of 2.0 and is naturally acidic. When mixed with vitamins and other additives in the lemon juice normally found in stores for human consumption, the pH is slightly less acidic with a pH measure of between 2.2 and 3.0. Due to the natural acidicy of lemon juice, it can be used to conduct electricity. How Can You Use Lemon Juice to Conduct Electricity? Since lemon juice is acidic, it will create both positive and negative ions when sitting in the naturally occurring water contained Read More
Java Method
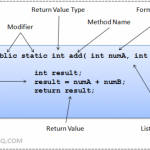
Java Method is very much similar to a normal method or a function written within a class definition. Java method is basically a set of statements group together to perform a specific task. This method is included in a class. An object instantiated from a class can call methods of that class. Every Java method has a basic structure which must be followed to create any type of method. This structure of a Java method holds the following components: Method Header [Modifiers + Return Value Type + Method Name + Read More


Share on: