Auditing enables you to determine which activities are occurring on your system and allows you to track access to objects, files and folders; and modifications made to the objects, files and folders. Auditing also enables you to collect information associated with resource access and usage on your system by allowing you to audit system logon, file access, and object access. Security auditing events are written to the Security log of the system and can be accessed from Event Viewer. Because event logs grow over time and typically consume valuable disk Read More
Coaxial Cable
Coaxial cable, also called coax, is used to transmit radio frequency (RF) signals. It has low emission losses and provides protection from electromagnetic interference, allowing signals with low power to be transmitted over longer distances. Coaxial cable is comprised of an inner core, insulator, shield, and outer cover. It is called coaxial because these sections all share the same axis. There are many different types of coaxial cable, each one with different physical and electronic properties designed for specific tasks. It is commonly used for carrying cable television signals along Read More
Error 0x8000ffff
Microsoft has bundled their basic Firewall application with the Windows Operating System (OS) since Windows XP SP 3. The firewall is used to provide consistent protection against Internet intrusion and attacks on computers and will block connection attempts that have previously been associated with malicious behavior. Error 0x8000ffff can be generated when the Microsoft Firewall Service fails to start or has a corrupted firewall rule. Although many Windows users disable their computer’s firewall connection when this error is triggered, it leaves the PC exposed to attacks. Therefore, the firewall should Read More
How to Convert DVD to AVI

Although movies stored in DVD format are high quality and can be ripped or copied to a consumer’s personal computer, they are bloated in size (3-9 gigabytes per movies) and have weird or obscure file naming conventions. By converting a DVD to AVI or other formats, before storing on a computer or portable hard disk a significant space savings can be obtained and the file naming can be tailored to meet personal preferences by the end user. A popular open source project supported on the Windows, Linux, and Mac OS Read More
Can Google Plus be Used for Business?

Google Plus is a social networking website that Google sponsors, which allows users to communicate in ways that other social networking websites have not implemented. For example, Circles is a Google Plus feature that allows users to separate contacts into multiple groups and only allows members of specific groups to see the users’ status updates. While Google Plus also allows users to create profiles and message friends in the same way that other social networking websites do, its unique features separate Google Plus from similar services. Current Google + Read More
What is a Pitot Tube?

A pitot tube measures pressure levels in liquids. They are most commonly seen in laboratory settings but can be seen in industrial applications as small cylinders. While a pitot tube is not the only device that measures fluid pressure, it is capable of being implemented in much more diverse environments than similar devices. How Pitot Tubes Work A pitot tube is simply a small cylinder that faces a fluid so that the fluid can enter it. Because the cylinder is open on one side and enclosed on the other, fluid Read More
How an Air Conditioner Works
Air conditioners work in much the same way that a refrigerator does; by cooling the air in an area while also extracting the hot air from the area and removing it from the vicinity. However, unlike a refrigerator, an air conditioner must do its job on an entire house, does not need to cool the air to the same degree, and it does so with some larger, more powerful equipment. The process of understanding an air conditioner cooling system should start with an examination of the different parts of an Read More
Automatic Number Plate Recognition
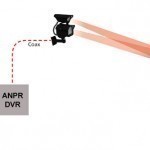
Automatic number plate recognition is a system designed to automatically recognize and store license plate number data on vehicles passing through a certain point. This is one of the mass surveillance systems that utilize optical character recognition programs and hardware capable of reading 1 plate/second off vehicles running at a maximum of 160 km/hr. Some systems make use of infrared cameras to increase the efficiency of the system. The automatic number plate recognition system can be used to monitor traffic, enforce traffic rules and regulations, collect electronic tolls, etc. Automatic Read More
Computer Virus

A computer virus is a program which reproduces itself. It may attach to other programs, it may create copies of itself (as in companion viruses). It may damage or corrupt data, change data, or degrade the performance of your system by utilizing resources such as memory or disk space. Types of Computer Viruses A computer virus may be categorized with one or more of the following four designations: Boot sector computer virus Master Boot Record (MBR) computer virus File infector computer virus Macro computer virus A computer virus which displays Read More
Jitter
Jitter is a variation or dislocation in the pulses of a digital transmission; it may be thought of, in a way, as irregular pulses. Jitter can manifest through variations in amplitude, signal strength, and other elements of such waves. The usual causes include connection timeouts, connection time lags, data traffic congestion, and interference. Simply put, this jitter is an undesirable output of system flaws and interruptions. To understand jitter, one must remember that data (whether audio, video, pictures or text) is seldom sent out wholly. Data is split up into Read More


Share on: