Web Design Tutorials Welcome to ByteGuide’s Web Design tutorials section. Web design is not just about creating a website. It also tackles other aspects like HTML, CSS Lay outing, how to get traffic, advertising, and SEO. In this section, we enlisted everything that you need for you to learn the basics of creating a website and how to earn money from it. We also provided information on how to keep you website secured from hackers. Our Web Design tutorials are easy to follow as it comes with illustrations and step Read More
Striping
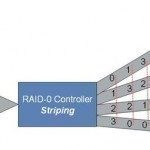
Striping is the automated process of writing data across multiple drives simulteneously. Striping is used to increase the performance of disk reads. When using striping, if you write a 5GB file across 5 drives, 1GB of data is written to each drive. Parallel reading of data from multiple disks can have a significant positive impact on performance, because the physical disk drive is most often the performance bottleneck. Striping is used in RAID Level 0. If one drive in a striped set fails, all of the data in the stripe Read More
Free Accounting Software
Everyone understands that they need to manage their finances but many people do not keep up with this task as often or as well as they should. This is mostly due to the fact that many people are simply overwhelmed with their financial information and have no idea how to keep track of it. Some people hire personal accountants to manage their money for them but the majority of people cannot afford such luxuries. Fortunately, there are many free accounting programs out there that can manage personal finances almost as Read More
Computer Telephony Software
Computer telephony software can be divided into a number of categories, each of which provides a set of functionality for Computer Telephony Integration (CTI). Automatic Call Distributors (ACD’s) Automatic Call Distributors are used by inbound call-centers to evenly distribute telephone calls between available customer service representatives. Interactive Voice Response (IVR) Interactive Voice Response systems are used to gather data from callers before transferring them to a customer service representative. IVR systems are well known for their frequent repetition of “Press or say 1 for …”. Screen Population Screen pop programs Read More
PXE Boot
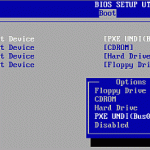
PXE Boot (Pre-eXecution Environment) is a protocol that boots computers without using a hard drive or an operating system. It is often used in industrial computers that do not require a graphical user interface, but require other applications to be run. PXE Boot is run over a network of computers and may or may not include Internet access. It is almost exclusively used in systems that are connected to a central server and uses subsequent computers to run virtual operating systems or DOS-like APIs. How PXE Boot Works PXE Boot Read More
L1 Cache

The L1 cache refers to the first tier in a computer processor’s memory cache system that increases the speed at which the processor delivers results to the user. The L1 cache sits between the processor and the computer’s RAM (Random Access Memory) and stores the user’s most accessed data in order for the processor to find data quicker. The L1 cache is usually between 8 KB and 64 KB in size, making it the smallest memory cache in a multi-level cache system. How L1 Cache Works Because the L1 cache Read More
Heaps
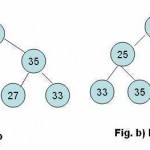
A heap is a binary tree that satisfies the following properties: Shape property Order property By the shape property, we mean that a heap must be a complete binary tree. A complete binary tree has all its levels filled, except possibly for the last, where the leaves must be located as far to the left as possible. By the order property, we mean that for every node in the heap, the value stored in that node is greater than or equal to the value in each of its children. A Read More
How to Add Music to Windows Media Player Library
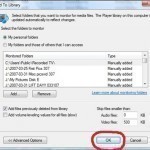
The Windows Media Player (WMP) Library collates, arranges, and creates play lists from the music and video files on a Windows computer. Once music files are added to the WMP Library, they can be played, burned to CD or DVD, streamed to other devices at home, or synced to portable media players. The current Windows Media Player version lets users add files to the library through one of several methods including: 1 – Monitoring folders that automatically search known music, video, and picture folders on the computer, including in the Read More
Securing Mail Servers
Mail Server Role Security Issues Mail servers store e-mail data, process client requests, and receive incoming e-mail from the Internet. The Post Office Protocol 3 (POP3) protocol provides clients with mailboxes and enables mail to be retrieved from the mail server. The e-mail accounts of users are POP3 accounts, and are stored on the configured mail server. POP3 makes is possible for clients to use Microsoft Outlook, or some other e-mail client to retrieve e-mail from the mail server. The Simple Mail Transfer Protocol (SMTP) protocol is utilized to transfer Read More
How to Use the Unix Top Command
Top is a small, but powerful program on both Unix and Linux systems. Its purpose is to allow users to monitor processes on their system. It has two main sections. The first displays general information such as the load averages, number of running and sleeping tasks, and overall CPU and memory usage. The second main section displays a sorted list of processes (usually by CPU usage) and shows their PIDs (Process ID number), the user who owns the process, running time, and CPU and memory that the process uses. As Read More


Share on: