The planet Mars has held a place of intrigue with humanity for many centuries. Also known as the “Red Planet,” Mars can be seen with the naked eye and looks red due to the large red desert covering its surface and the presence of a large amount of ferric oxide. As the fourth planet in the solar system, and final one before the asteroid belt, a common question that arises amongst students and adults is what is Mars made of? Is Mars Made of Similar Material to Earth? The basic Read More
Technologies That Can Help Protect Your Privacy

In a previous article on privacy we’ve established what it is, how does digitally networking our world affect it, and in a nutshell, why should we care. We established that the best way to ensure your privacy is through technological means, and in this article I offer an overview of what such technologies are. What is common to all of them is that they let you control access to information about yourself, whether it is your location, sites you visit, conversations you have online, things you post about yourself, and Read More
Inverse Square Law
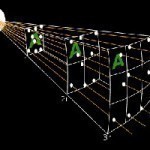
The Inverse Square Law is a physics law that states that a strength or quantity is inversely proportional to the square of the distance from the source of the strength or quantity. In more technical terms, a vector field divergence that is a result of the radial inverse square law fields with one or many sources, is proportional to the strength of the local sources and no outside sources. What is the Justification for the Inverse Square Law? The inverse square law applies whenever an energy, force, or conserved quantity Read More
Backing Up and Restoring the WINS Database
Protecting the WINS database To protect your WINS databases from disasters and corruption, you should regularly back up your WINS databases. The methods which you can use to back up the WINS database are: You can use the WINS console to perform: A manual back up of the WINS database Schedule an automatic backup of the WINS database. You can use the ntbackup.exe utility to back up the WINS database. The Windows Server 2003 Volume Shadow Copy feature allows you to back up the WINS database while it is online. Read More
DNA Fingerprinting
DNA fingerprinting is the process of taking a cell sample from a person and analyzing it. This technique involves analyses of less than 0.1% of human DNA (which is different for each person). Though small, this 0.1% of DNA is enough to distinguish one individual from another and can be used to determine maternity/ paternity or the identity of a person, whether dead or alive. DNA fingerprinting should not be confused with the traditional idea of fingerprinting (making an imprint of a person’s fingerprints in ink). What is DNA? Every Read More
Photo Shop Tutorials
Photo Shop Tutorials Check out our free Photoshop tutorials and learn how to use the application in creating presentations! Sleek Navigation Interface This tutorial will show you how to make a sleek tabbed navigation interface for your web site. Sidebar Menu Design This PhotoShop tutorial will show you how to make a slick sidebar menu for your web site. Purple Theme Navigation This tutorial shows you how to make a navigation system for your website with a nice purple theme. Melting Icy Topography In this PhotoShop tutorial, you will learn Read More
How to Convert AVI to MPEG

The AVI (Audio Video Interleave) file format was first created by Microsoft in late 1992 as part of the company’s video for Windows technology efforts. An AVI file can consist of both audio and video content that permits synchronous playback. The majority of AVI files use the format extension defined by the Matrox OpenDML group in February 1996. A common problem that arises for end-users is to convert AVI to MPEG format to support playback on a greater number of multimedia playback devices. Convert AVI to MPEG with HandBrake Step Read More
Flatbed Scanner – Pros and Cons

A flatbed scanner is a device that is able to scan a document and then convert what it has read into digital information. Flatbed scanners are different from other types of scanner because flatbed scanners allow the user to simply lay the document down on the machine, close the lid, and scan both sides of the document simultaneously within a matter of seconds. There are many different types of scanners but this article will focus on the pros and cons of flatbed scanners. Pros 1. Quality Flatbed scanners have a Read More
DVD Player Software
AVS DVD Player Play movie DVDs, video & audio files right on your computer with FREE AVS DVD Player. AVS DVD Player is a compact and easy-to-use program that has a simple user-friendly interface allowing you to start watching DVD movies with no additional software. ClipRex Cliprex DVD Player Professional software is the free solution for playing DVDs on the PC. Cliprex DVD Player Professional will handle playback of both commercial and consumer-created DVDs. Beside DVD video it supports most well known video standard formats, like DIVX, XVID, MPEG, WMV, Read More
Implementing Public Key Infrastructure
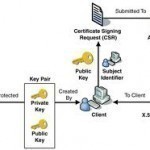
An Overview on the Public Key Infrastructure (PKI) A set of components, standards, and protocols make up the Public Key Infrastructure (PKI), which protects data as it is transmitted over the network. The PKI is an integral aspect of security within a network. Digital certificates form the basis of the PKI because these certificates use cryptographic algorithms and key lengths to protect data as it is transmitted over the network. The more important components of the PKI are summarized below: Cryptographic components are the encryption and hashing algorithms that are Read More


Share on: